| Michael Horowitz |
Home => Killing Windows Update on Windows 10
|
| Michael Horowitz |
Home => Killing Windows Update on Windows 10
|
| [Formatted for Printing] | From the personal web site of Michael Horowitz |
Initial release: December 5, 2018 | Last Updated: January 8, 2019
Comments on this article are at askwoody.com.
Microsoft can not conceive of a valid reason for a Windows 10 user not to want the latest bug fixes. Bug fixes good, is their corporate mantra. They are, however, wrong. Not only are there many instances where stability trumps patches, they have shown over and over again that their patches are not to be trusted. Just this week, Windows 10 bug fixes caused the Surface Book 2 to crash.
My recent blog Defending against Windows 10 bug fixes discussed many options for postponing bug fixes but none, other than keeping the computer off-line, are foolproof. The most interesting section of that very long blog is A full frontal attack on Windows Update. This is a simplified, cheat sheet, version of that section.
Back on Windows 7, it was so much easier to disable Windows Update, there was just one service to worry about. Those were the good old days. With Windows 10, there are three aspects to disabling Windows Update: shutting down multiple Services, disabling many Scheduled Tasks and preventing the parts of Windows Update that can not be easily shut down from phoning home. Microsoft has limited the first two options, some services and started tasks can not be disabled, even by Administrative users. And, like the Walking Dead, some services and tasks that we can disable, get re-enabled over time by the ones that can not be disabled. That leaves the Windows Firewall as our biggest hammer.
Every Windows Service and Scheduled Task referred to below is not installed on every Windows 10 machine. This is because Windows Update keeps changing, in large part, to prevent people from doing just this.
Note that this is not well worn territory, and I do not claim to be an expert on Windows Update.
Try to disable all the services involved with Windows Update.
You should be able to disable the legacy Windows Update Service (wuauserv) and the Windows Remediation Service (sedsvc).
Windows 10 Update Facilitation Service (osrss) can not be stopped or disabled.My experience with the other two services (Update Orchestrator Service (UsoSvc) and Windows Update Medic Service (WaaSMedicSvc) has been inconsistent.
As with Services, try to disable all the Scheduled Tasks you can. Note that whatever software you use to deal with scheduled tasks, it must run as an Admin user. There are some tasks that restricted/standard users can not even see. (Updated Dec 8, 2018)
I have not seen, but have read about other Windows Update related scheduled tasks: USO_UxBroker_Display, USO_UxBroker_ReadyToReboot, Policy Install and Resume On Boot.
For dealing with the Windows Task Scheduler, I suggest TaskSchedulerView by Nir Sofer. It is free, portable and from a trustworthy source.
While some Services and Started Tasks are off-limits, everything can be blocked in the Windows firewall.
Perhaps my big contribution here is the idea of blocking a Windows service from phoning home. Firewalls traditionally block ports, IP addresses and programs but the Windows firewall can also block a Windows Service. We need this since many services run under the svchost.exe program.
To block a Service
Do this for every Windows Update service on the PC: Windows Update, Windows Update Medic, Windows Remediation, Update Orchestrator and Windows 10 Update Facilitation.
These Windows Update related programs definitely phone home to Microsoft, so they should be blocked too.
The click stream for blocking a program is a bit different from blocking a service. It is:
These Windows Update related programs may or may not phone home to Microsoft, I don't know. To be fully protected, they should be blocked with an outbound firewall rule too.
In the end, your firewall rules will look something like those below.
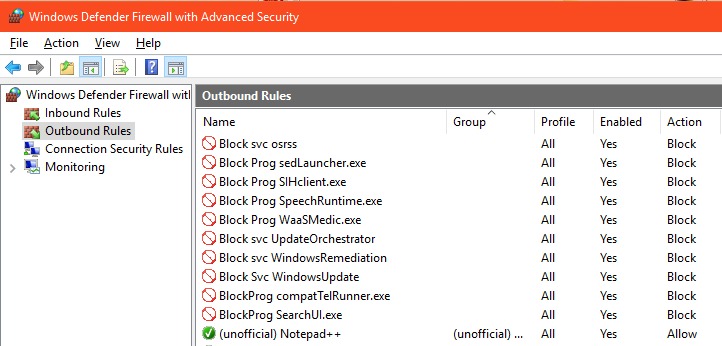
The Windows Remediation Service (sedsvc) is C:\Program Files\rempl\sedsvc.exe. Blocking the Service may be sufficient, but to be thorough, you can block it as a program too. According to this article, these other programs are also involved in Windows Update: eosnotify.exe, windows10upgraderapp.exe, remsh.exe (pretty sure this has been retired), dismHost.exe, InstallAgent.exe and Windows10Upgrade.exe. I have not seen them. A user comment to this article also mentions the Windows10UpgraderApp.exe but adds that it is in the C:\Window10Upgrade folder. (Updated Dec 6, 2018)
Outbound firewall rules can also be used to prevent Windows 10 telemetry from phoning home to Microsoft, but that's another whole topic. In the image above, compatTelRunner.exe is telemetry and SearchUI.exe is Cortana.
It would be nice to know the fewest changes needed to block Windows Update on Windows 10 but that is likely to change over time, so it doesn't pay to invest a lot of effort into answering the question.
As thorough as all this may seem, there may well be registry zaps that let you disable the Services and Started Tasks that are normally off-limits. I have not looked into this. If Windows Update can not phone home, then it is not critical to prevent every part of it from executing.
Which begs the question, is Windows Update still phoning home? A great program that helps answer this question is TcpLogView by Nir Softer. It shows every IP address your computer makes an outbound connection to and the process or program that made the connection. Often, it also shows the name of the contacted computer. (Added Dec 7, 2018)
Of course, if you succeed in blocking patches, at some point you will want or need them. To maintain the most control, see the section on Manual Updating in my earlier blog. (Added Dec 5, 2018)
Finally, there are still other ways to attack Windows Update. Reddit user WelshWorker explained his procedure in PERMANENTLY Disabling Windows 10 Upgrade Assistant to stay on one build. His additional steps include blocking 15 domains used by Windows Update, removing all permissions from three Windows Update folders, creating firewall rules to block network communication for the .EXE files in those folders and deleting the contents of the SoftwareDistribution folder. He also has a script to automate some of it.
Makes the stuff above seem not so paranoid.
| | ||
| @defensivecomput | TOP | Home => Killing Windows Update on Windows 10 |
| michael--at--michaelhorowitz.com | Last Updated: January 8, 2019 5 PM | ||

Copyright 2001-2024 |
Copyright 2001-2024 |