| Michael Horowitz |
Home => Defending against Windows 10 bug fixes
|
| Michael Horowitz |
Home => Defending against Windows 10 bug fixes
|
| [Formatted for Printing] | From the personal web site of Michael Horowitz |
Last Updated: October 11, 2019 5 PM
Update History: October 20, 21, 22, 25, 26 and 29. Also, November 2, 4, 6, 7, 10, 11, 13, 14, 15, 16, 17 yada yada yada)
Initial release: October 19, 2018
Comments on this article are at askwoody.com
Software always needs bug fixes. Still, it is widely understood that Windows Update, which installs bug fixes for Windows, is itself dangerous. Too many bug fixes create new problems. It has gotten so bad that every techie paying attention knows to wait before installing the latest "updates." Let someone else experience the inevitable bugs that new fixes create.
This reached it apex a few days ago when installing updates to Windows 10 wiped out all your files. Worse still, Microsoft was warned about that problem and ignored the warning. Just disgraceful. Then too, the October round of Windows bug fixes disabled audio for some people and caused some HP computers to crash.
How long to wait, is a matter of opinion. Personally, I wait at least 3 weeks before installing the monthly Windows 7 Patch Tuesday bug fixes. Someone could argue that during these 3 weeks the systems that I manage are vulnerable to the latest flaws which bad guys reverse engineer and begin exploiting pretty quickly. To this, I say that there is no single obviously right answer. Any patching schedule entails some risk.
At least with Windows 7 and 8, we are in total control of the patching schedule. Windows 10, however, complicates things a lot.
Unlike earlier versions of Windows, Windows 10 is totally re-built twice a year. These rebuilt versions are equivalent to what Microsoft used to call a Service Pack. It is a new starting point for the operating system, one that includes both new features and bug fixes. In September 2017 (more or less) Microsoft released the 1709 edition/service pack of Windows 10. In April (more or less) they released the 1803 edition and in October 2018 they released a Windows 10 service pack called 1809.
These Windows 10 service pack editions are then supported with bug fixes for a while (details below). These bug fixes are released roughly twice a month. For the 1803 Service Pack, the most recent bug fixes were released on October 9th, September 26th, 17th and 11th, August 30th and 14th and July 24th, 16th and 10th.
At some point, bug fixes for each Windows 10 Service Pack stop, and users are forced to upgrade to a newer service pack release. This upgrade is a pain; it is time consuming (especially on older hardware) and very much like a total re-install of the system. Many preferences are reset to the way Microsoft wants them, which is often not what the end user wants.
Avoiding the upgrade hassle costs money.
Microsoft's best customers are rewarded with the least hassle, they are forced to install new Service Packs far less frequently than the rest of us. The Enterprise and Education editions of Windows 10 get bug fixes for 2.5 years from their release date. The Professional Edition gets Service Pack bug fixes for 1.5 years. Thus, the Professional Edition of Service Pack 1703, which was released in April 2017, died in October 2018. Service Pack 1709 will stop getting bug fixes in April 2019 and 1803 will stop being updated in November 2019. (updated Oct 21,2018)
Of course, this assumes that users were able to delay the forced installation of newer Service Packs. The more expensive Professional edition, can delay the forced install of a new service pack by configuring some system settings (much more below). Users of the cheap Home Edition, have to research hacking the registry, there is no user interface for delaying a new Service Pack. Even then, it is not clear that the Home Edition pays any attention to the registry updates. Home Edition users will be installing new Service Packs twice a year. (updated Nov 16, 2018)
The more money you give Microsoft, the better you get treated.
And then, we have yet another version of Windows for the big boys only: LTSB. If a company plans well, and avoids the obstacles Microsoft puts in their way, they can run a stable copy of Windows 10 with bug fixes for 10 years. Gregg Keizer of Computerworld wrote about this on Nov 13, 2018.
Every two or three years, Microsoft designates a particular Windows 10 Service Pack as an LTSB edition. The first LTSB was based on the initial July 2015 release of the system, the second one was based on Service Pack 1607 and a third one is due any day (it was supposed to be based on 1809). LTSB releases get bug fixes for five years out of the box. Customers can pay more for "Software Assurance" to extend this to 10 years.
To achieve stability, the LTSB edition throws some things overboard. It is missing the Edge browser, Cortana, the Microsoft Store and UWP (Universal Windows Platform, tile world) apps. Sign me up! Microsoft says LTSB is meant for ATMs and PCs that control industrial systems, medical equipment or point-of-sale devices. But, LTSB may have been so appealing that companies were using it for their employees too. I would have.
In early 2017, Microsoft changed the rules: bug fixes will only be offered on CPUs that were available when the LTSB version was first released. So, if the Intel Core i series was at the fourth generation when Service Pack 1607 (officially Windows 10 Enterprise 2016 LTSB) was released, then there are no bug fixes for W10E2016LTSB if it is running on a 5th or 6th or 7th generation CPU.
Microsoft even screws the big boys.
April 17, 2019: Steve Gibson refers to LTSB as LTSC, Long Term Service Channel. On his Security Now podcast he noted that it does not have Cortana or Edge. Also, no Tile World apps. See a screen shot of the start menu. He got access by paying $800/year for an MSDN subscription.
October 9, 2019: The Windows lifecycle fact sheet from Microsoft has two sections. The first applies to Windows 10 Home, Enterprise, Education, Pro, and Pro for Workstations editions. The second applies to Enterprise LTSC/LTSB editions. This is official documentation of the difference.
In Windows 10 Professional, the user interface for delaying bug fixes and service packs is about as confusing as it could possibly be. In my opinion, this is not an accident, I feel that the user interface was purposely designed to trick as many people as possible into not delaying anything. In this regard, I regard Microsoft as the enemy, not the friend of Windows users. Too extreme? Read on.
Anyone using Windows has logged on to the operating system with a userid/password. There are two important classes of Windows users: administrators and restricted users. Administrators have full run of the place, they can do anything they please (I am simplifying a bit). Restricted users, which Windows 10 refers to as Standard users, are restricted in what they can do.
The Defensive Computing approach is to logon as a restricted user. I do so all the time; so too do my clients. It's safer that way. For example, if anything malicious gets onto the computer, it is limited in the damage it can cause. Restricted users see the same system settings as Administrators but should they attempt to do something that can screw up the system, such as stopping a service, disabling a device in Device Manager or installing new software, they have to first provide the password for an Administrator user.
That's the way Windows works almost all the time. The one exception is this, delaying the installation of Windows 10 bug fixes and Service Packs. In this case, Restricted/Standard users don't even see the options to delay things. Only when logged on to Windows as an Administrator are the controls described later visible.
If you are following along at home, go to System Settings -> Update and Security -> Windows Update (should be the default) -> Advanced Options.
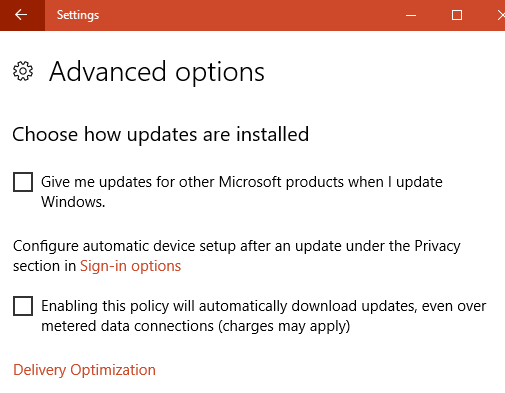
Above are the advanced options for Windows Update as shown to a Restricted/Standard user (screen shot from service pack 1709). There is nothing about delaying bug fixes.
In contrast, the Advanced Options for Administrators are shown below. There are three options for choosing when updates are installed (which translates to delaying bug fixes).
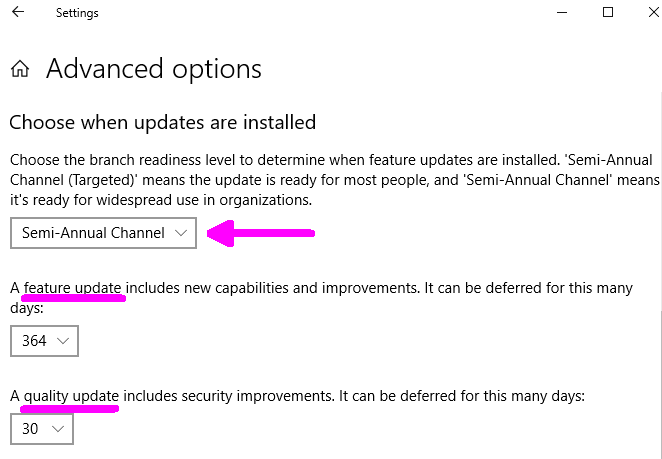
The three visible settings have names that make no sense, which I take as evidence that Microsoft wants to shove bug fixes down the throats of their customers.
The first setting is branch readiness (see what I mean?) which offers a choice of two branch channels.
What is a branch channel? Good question, as the terminology here has changed during the lifetime of Windows 10. Simply put, a branch channel refers to the age of a given Service Pack (1709, 1803, 1809, etc.). One branch channel refers to a new Service Pack, the other to a slightly older one.
Each of the branch channels are called Semi-Annual, a reference to the twice-a-year Service Pack releases of Windows 10. One is just plain Semi-Annual, the other adds the word "Targeted". According to Microsoft, the targeted branch channel is for "most people" and the non targeted branch is for "widespread use in organizations." Got that?
Translating this doublespeak into English, as best I can, the one for "most people" is newer, the one for "widespread use in organizations" is older. Older Service Packs are more reliable, so this is what I recommend. According to Woody Leonhard, other euphemisms Microsoft has used for "we have fixed the most egregious bugs in this service pack" are "ready for widespread deployment" and "full availability." Non techies, who have not read this article, are used as guinea pigs. They experience all the bugs in a new Service Pack, while those of us in the know, wait for most obvious bugs to be fixed, before installing the same Service Pack.
To illustrate, the 1803 service pack of Windows 10 was released to the public (the "most people" branch channel) on April 30, 2018. It was released to the "widespread use in organizations" branch channel about 2.5 months later (July 10,2018). The previous 1709 service pack, was first released October 17, 2017 but not released to the "widespread use in organizations" branch channel until January 18, 2018.
When a Service Pack is first released to the public, it is installed on the Home Edition customers. Currently, in October 2018, the 1809 service pack of Windows 10 is being sent to Home Edition users. A Professional edition of Windows 10, that is configured for the "widespread use in organizations" branch channel, will not get the 1809 edition for a few months. This is, perhaps, the best reason to pay more for the Professional edition.
The next option is for Feature Updates. What is a Feature Update? It is a Service Pack. Here you can defer the installation of a Service Pack for a certain number of days, up to 365. If you were paying attention, the just-discussed Branch Channel option also delayed the installation of Service Packs. How do these two options relate to each other? Beats me.
Also not explained is the exact definition of the number of days. That is, what is the starting point when counting days? Today? When the Service Pack was first released? When it first hit the "widespread use in organizations" branch channel? April Fools day? And, for that matter, to which Service Pack does the delay even apply? On a copy of Windows 10 version 1709, does the delay apply to the 1803 Service Pack or the 1809 Service Pack? Microsoft does not say and some experts disagree.
On November 14, 2018 an argument about this broke out at askwoody.com. Susan Bradley wrote that "if you do choose a deferral period of 365 days, and you have Pro version, you will be deferring yourself into an unsupported condition." She meant that you would end up running the currently installed Service Pack well after the last bug fixes were released for it. In turn, this implies that the 365 day deferral starts TODAY. But, a reader disagreed and cited an October 2018 article by Windows expert Ed Bott where Bott wrote "you can defer the delivery of feature updates by up to 365 days from the official release date for the selected channel." Since each Service Pack is supported for 1.5 years, this means you can not use this feature to run a service pack past its life span (more than 1.5 years). Sounds reasonable. A different reader cited his personal experience noting that on Nov. 14, 2018 a computer with a 365 deferral was still running Service Pack 1703, further proof that the deferral is with respect to when a new service pack is offered, not from when you last installed a service pack. The final article that convinced me that the starting point is the release date of a Service Pack was a Nov 15, 2018 by Woody Leonhard (How to upgrade to the version of Win10 Pro that YOU want) where he discusses how someone on 1703 should calculate and configure the number of delay days to get Windows Update to install either Service Pack 1709 or 1803. (Added Nov 15, 2018)
Whatever the definition, the safest option is to delay it as long as possible.
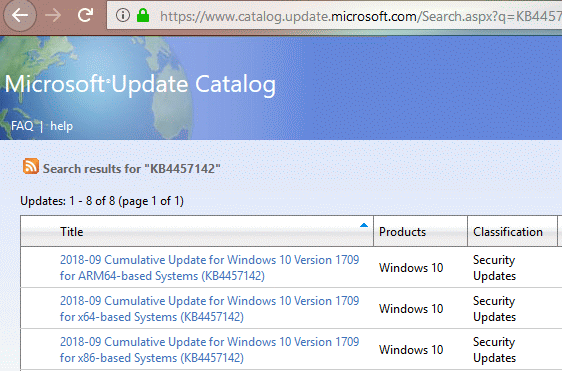
The last option involves a Quality Update. Confused about the term Quality Update? You should be, Microsoft is inconsistent in their terminology. Simply put, a Quality Update refers to bug fixes to a Service Pack. As shown below, in a screen shot of the Microsoft Catalog, these bug fixes are also referred to as Cumulative Updates and Security Updates. The only consistency is the word update, a euphemism for fixing a mistake.
We have seen the rise of euphemisms before. George Carlin did a bit about the effect of combat on soldiers. In the first World War, soldiers suffered from shell shock. Simple, honest, direct language. By the second World War, the same condition was called battle fatigue. In the Korean war it was referred to as operational exhaustion and by the Vietnam war it was Post Traumatic Stress Disorder.
You may have noticed that I am a shell shock kind of guy. In this article, bug fixes are bug fixes, not updates. Ditto for Service Packs. My intention is to explain, Microsoft's intention is to make Post Traumatic Stress Disorder out of shell shock.
Getting back to the main point, the installation of bug fixes to the currently installed Windows 10 Service Pack can be delayed for up to 30 days. I suggest setting this to 30 days.
There is no one right answer when it comes to how long to delay the installation of Service Packs and the bug fixes to them. Woody Leonhard, writing in Computerworld, suggests that the sweet spot is delaying a Service Pack for 60 or 90 days and delaying the twice-a-month bug fixes for 10 or 12 or more days. If a major problem with a patch arises, then he suggests upping the deferral to 30 days. Of course, this assumes you are always watching and thus aware of problems with patches. I would delay longer. (Added Nov. 2, 2018)
There are still more Windows Update gotchas to be aware of.
The three settings discussed above are fine, except when they are not. Woody Leonhard warns about Microsoft ignoring its own rules:
"On three separate occasions in the past year - in November 2017, January 2018, and March 2018 - Microsoft forcibly upgraded Windows 10 Pro machines that have Advanced Options set to defer upgrades. Microsoft has, in effect, ignored its own settings ... These aren't fly-by-night reports, or wails of pain from users who forgot to turn something on or off. All three have been documented by Microsoft as being Microsoft mistakes, in nooks and crannies of its various posts. Oddly, it seems that the metered connection trick kept working in the face of all of those 'oopsies.' You may well want to set your internet connection to metered, even if you use Windows 10 Pro, Enterprise or Education."
More on metered connections below.
Another case where these delaying tacts may not be honored is in the Home Edition of Windows 10. I have not tested this myself. Woody Leonhard claims they are not honored. And, why would they, there is no user interface for the delaying settings on the Home Edition. On the Oct. 23, 2018 edition of the Security Now podcast, Steve Gibson mentioned that he upgraded the Windows 10 Home Edition computer he uses for the podcast to the Professional Edition, just so that he could delay bug fixes. (added Oct. 26, 2018)
There are, however, Registry zaps availble to Home Edition users. For example, you can find instructions at ghacks.net for updating the Windows Registry to enable the same delaying options available in the Professional Edition. An AskWoody.com user also posted registry updates that were based on this Microsoft documentation. (Updated Dec 11, 2018)Yet another instance where the just-discussed delaying settings are ignored is when you explicitly ask Windows to check for updates. This was not always the case, but it is now.
This was recently explained (Oct 2018) by Chris Hoffman of How To Geek who wrote: "When you click the “Check for Updates” button, Microsoft gives you updates early, skipping a normal part of the testing process ... For now, this weirdness with the “Check for Updates” button only applies once every six months when a new major update to Windows 10 is released."
In Dec. 2018, Hoffman again addressed this in Watch Out: Clicking 'Check for Updates' Still Installs Unstable Updates on Windows 10 based on a blog posting by a Microsoft vice president. He again warned that "Microsoft hasn't learned its lesson. If you click the 'Check for Updates' button in the Settings app, Microsoft ... will give you 'preview' updates that haven’t gone through the normal testing process ... Once again, Microsoft is using everyone who clicks 'Check for Updates' as a beta tester. Don’t click this button unless you want unstable updates." (Added Dec 11, 2018)
Woody Leonhard first noticed this behavior in May with the release of Service Pack 1803. He wrote: "Some people, when clicking on 'Check for updates' in Win10 1703 or 1709, were pushed into the Win10 1803 upgrade sequence." So, while this is not new, at least John Cable of Microsoft was clear about it in an October 2nd blog posting, How to get the Windows 10 October 2018 Update where he wrote "...we encourage you to wait until the update is offered to your device..." (added Oct. 22, 2018)
So, instead of installing bug fixes for the current Service Pack, which would make a computer more reliable, clicking this button might install a brand new Service Pack, making the computer less reliable, not to mention depriving you of use of the computer for an hour or two or three while the Service Pack installs itself and resets many of the configuration options you changed. (added Oct. 22, 2018)
And, making a bad situation worse, Hoffman points out that once Windows Update starts downloading an update, you can not stop it.
Turning back to defense, Microsoft offers Administrator class users, a get out of jail free card for Windows 10 bug fixes. It's not a full pardon, just a brief break.
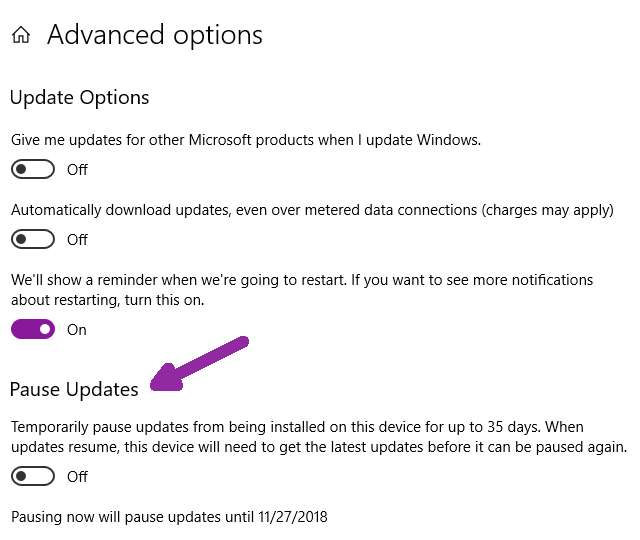
As shown above, Administrators can pause the installation of bug fixes ("updates") for 35 days. The description of this says you can pause for "up to" 35 days, this is not true. On Service Pack 1803 it paused for 35 days, there was no choice as to the number of days. On October 25th, it claimed to pause updates until November 29th. To see this option, go to Settings -> Update and Security -> Advanced Options. When this (stay) arm wrestles with the Check for Updates (go) button, I don't know who wins.
As far as I know this is not an option on the Home Edition of Windows 10, even for Administrators that are willing to update the registry.
Another defensive step against Windows bug fixes is avoiding driver updates. This is particularly timely as the October 2018 patches included not one, but two bad drivers.
There is a way to prevent Windows update from installing new drivers, but it is hidden, even from Administrators. In fact, it is not included in the System Settings at all. Instead, this is controlled with the Local Group Policy Editor. See what I mean about Microsoft being the enemy.
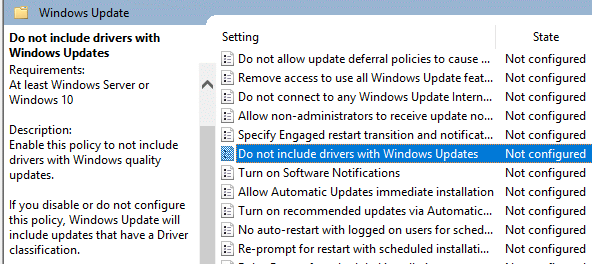
The procedure is described in detail by Mauro Huculak in How to disable automatic driver updates on Windows 10 (Aug. 2018). In brief, you run gpedit.msc, go to Computer Configuration -> Administrative Templates -> Windows Components -> Windows Update and look for the "Do not include drivers with Windows Update" policy. As with the other Windows Update tweaks, this one too requires Home Edition users to hack away at the registry. The Huculak article has the details.
There is also a long discussion of How to disable Win10 driver updates over at AskWoody.com from December 2018.
Of course, sometimes you need, or want, to update a driver. For that, see the section on Manual Updating below.
In a quote above, Woody Leonhard pointed out that a metered connection has been known to delay the installation of a new Service Pack when other options were ignored. On the other hand, he also writes that "There's no guarantee this approach (dare I call it a 'trick'?) will always work."
Metered connections are not a new tactic and they are available in the Home, Professional, Enterprise and Education editions of Windows 10. Making this change, requires you to be logged on to Windows as an Administrator. The metered attribute needs to set for every Internet connection. A cellular data network connection is considered metered by default.
Start out with Settings -> Network and Internet.
For the Ethernet connection, click first on "Ethernet" in the left side vertical column, then click on the Ethernet connection in the middle of the page. It does not look clickable, but it is. On the resulting page, look for "Set as metered connection" and turn it on.
For wireless connections, click first on "Wi-Fi" in the left side vertical column, then click on "Manage known networks" to see a list of the Wi-Fi networks the Windows 10 computer has previously connected to. The option here is again called "Set as metered connection" but it needs to be set for each Wi-Fi network individually.
The good news is that you do not need to be connected to a particular network to change this option. The bad news, is that when the computer connects to a new Wi-Fi network, it will default to being un-metered.
One thing that always seems to be omitted from the discussion of Metered connections is the issue of being logged on to Windows as a restricted/standard user vs. an Administrator class user. My testing of this showed that restricted users can not change the Metered status. Worse, it is not at all clear that the setting even applies to Local restricted users because they always see it as OFF even when a Local Admin user sees it as ON.
My test results (all users are Local): On a Windows 10 Pro machine running Service Pack 1709, a restricted user sees the Metered status as OFF and it can not be changed. An Admin user, however, sees it as ON. I created a new restricted user and the result was the same. On a Windows 10 Pro machine running Service Pack 1803, a restricted user again saw the setting as OFF and could not change it. An admin user saw it ON on two Wi-Fi networks but one network let the value be changed while the setting was fixed on the other network. Go figure. On a Windows 10 Home machine running Service Pack 1709 (with only Wi-Fi) things were as expected for the admin user - all Wi-Fi networks were set as metered and the setting could be toggled for each network. Here too, a restricted saw each network as NOT metered and could not change the setting.
On Pro machines, a metered connection can also have data usage limits put on it (Settings -> Network and Internet -> Data Usage). This is not available on the Home Edition. An admin user on a Pro system can set a limit on the data used by each Wi-Fi network and/or by Ethernet. When data limits are being imposed, the connection is locked into a Metered status and it can not be changed as per: Why can't I change the metered connection setting?.
FYI: How, When, and Why to Set a Connection as Metered on Windows 10 at How-To Geek.
Worn out yet? If not, there is still another line of defense, Microsoft's Wushowhide program. It is not pre-installed, you need to find it, download it and configure it. Then, you need to run it often for it to be of any use in blocking new Service Packs. It sounds like quite a lot of work, but it is available on the Home Edition.
Woody Leonhard has written about it a couple times: How to block the Windows 10 October 2018 Update, version 1809, from installing and Woody’s Win10Tip: Apply updates carefully (Nov 2016).
The blocking methods mentioned so far have not pleased everyone, so third parties have created software to block Windows Update.
StopUpdates10 was written by someone named Dmitry and it is available from a blog entry at greatis.com. I have not tried it. It is free and works on Windows Home Edition. It claims to block executing of the Windows Update processes by creating the policy registry keys to block updates. What that means, I don't know. It also claims to stop the Windows Update service (which you can do yourself) and make sure that it stays stopped by checking on it every now and then. StopUpdates10 installs a system service, Updates Guard, that runs in the background. There is a Restore feature to undo the changes it makes. The documentation says that it blocks the execution of several processes used for updating, but does not say exactly what they are.
Another program is Windows Update Blocker, now at version 1.1. The program is free, portable and from Sordum.org. Who is Sordum.org? He/she/they don't say. I have not tried it. It is focused on the Windows Update service and seems to just give you a GUI to enabling and disabling it. That said, I found the description of the program confusing. For example, there are some references to zapping the Registry but they are not explained at all. It also says nothing about the Windows Update service being restarted by scheduled tasks. The program can also deal with other services but this requires you to edit a text file and I could not understand the meaning of the numbers used as flags in the file. It supports Windows 10, 8.1, 8, 7 and older.
One problem with stopping services is that there is more than one service to deal with. In addition to the legacy Windows Update service (wuauserv), there are three other services involved with Windows Update. Then too, there are quite a few Scheduled Tasks that are also involved with Windows Update, so good luck shutting everything down. For more on this see the Full Frontal Attack section below. (Modified Nov 29, 2018)
Another free (and portable) program is ShutUp10 from O and O Software. The program is focused on telemetry/spying but it includes a section devoted to Windows Update with 11 tweakable knobs. To me, the user interface is brutally confusing, I could make no sense of it. And, the program does not say what each knob does. Is it modifying the registry? Configuring a system setting? If so which one? Is it updating the firewall? When you click on an option you are given some explanation, but nothing that I found useful. (Added Nov 10, 2018)
Another approach is to block Windows Update access to the network. The idea being that even if the underlying services run, they can't phone home.
This is the approach taken by Windows 10 Firewall Control by Sphinx Software. It comes in multiple editions, one of which is free. I have not used it. My question here is exactly what does it block? Which programs? Which services? I asked Sphinx Software, and got a response, but it did not address the question. Here is a Dec. 2016 article about using the firewall. (Updated Nov 10, 2018)
Another program WindowsSpyBlocker is focused on blocking telemetry/spying, but it includes firewall based blocking of Windows update via IP addresses. The program is distributed as a single EXE file, but we can see and download the list of IP addresses it uses to block Windows Update. There is no way to just make these firewall changes without running the entire program. And, it is not clear if the firewall rules apply when the computer is using a VPN as that sends all traffic to a single VPN server. Then too, the list of IP addresses used by Windows Update is sure to change over time. So, rather than focus on IP addresses it probably more realistic to block the programs that underly the Windows services and started tasks in the Full Frontal Attack section below. (Added Nov 26, 2018)
To state the obvious, installing Windows software from people/companies/sources that you don't know, or know of, is always risky. This is especially true when the software is not totally transparent about what it does.
Everyone paying attention is well aware that Microsoft does a miserable job of explaining things. With that in mind, we have this How to configure automatic updates by using Group Policy or registry settings.
On the one hand, it was last updated in October 2018, so it should be current. On the other hand, it applies as far back as Windows Vista. And, it warns that option 5 is no longer available in Windows 10, yet there is no option 5. Typical Microsoft.
It says that there is an option, using Local Group Policy, to have Windows Update: Notify for download and notify for install. I don't believe it. When it warns that an option is not available in Windows 10, it is not clear if this refers to the Disabled option, the Not Configured option or both. It offers a registry update to disable Windows Update. I don't believe it. That said, I have not tested it.
Up till now, things have been inside the box. Now, lets step outside it.
The biggest hammer in our toolkit is the Internet. If a Windows 10 PC is kept off-line it can't update anything. Extreme, of course, yet there may be circumstances where it makes sense. Nothing to do with Windows, but any computer with particularly high value or sensitive files is best kept off the Internet. But, back to Windows, keep in mind that Microsoft Office spies on users, a great reason to keep a PC off-line. (Updated Nov 14, 2018)
A bit less extreme is to fill up the C disk. Windows Update needs a lot of hard disk space to do its thing and if the C disk has only a couple gigabytes of freespace, it can't function. Just keep your big files on a network drive, cloud storage or a USB flash drive. Who thinks like this? Someone (me) who purchased the lowest end PC that can run Windows 10, a machine where the entire C disk is 30GB (advertised as 32GB, of course). It should have been a crime for major Windows vendors to sell machines like this. On January 8, 2019 I expanded on this idea in Blocking Windows Update on Windows 10 with C disk freespace.
Update: Dec 5, 2018: A cheat sheet summary of this section is available here: Killing Windows Update on Windows 10
If you believe that the best defense is a good offense, then this is the approach for you. On November 2, 2018, Constantinos over at wintips.org wrote How To Turn Off Windows 10 Updates Permanently, in which he describes six attacks on Windows Update itself.
On Windows 7, all we had to do was disable the Windows Update service. But, things are much more complicated in Windows 10, which will, eventually, re-enable the Windows Update service. Windows Update on Windows 10 consists of multiple services and multiple scheduled tasks. Plus, some of the services can not be stopped or disabled in the usual manner, you have to zap the registry instead.
I have seen the five services listed below, each of which is somehow involved in Windows Update. But, every Windows 10 computer does not have every one of these services installed. (Updated Dec 3, 2018)
To disable the Windows Update Medic Service and the Update Orchestrator Service, Constantinos offers these registry zaps. Navigate to:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\WaaSMedicSvc
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\UsoSvc
and set the Start key to 4 (from 3). Again, you may or may not need this for the Update Orchestrator Service. (Updated Dec 7, 2018)
After disabling a service, Constantinos suggestions going to the LogOn tab and changing it from the Local System account to one of your accounts. Then, give it the wrong password! This insures that Microsoft can not re-enable the service. However, just as some services can not be disabled or stopped, this trick too does not work with all services. (Updated Dec 5, 2018)
- - - - - - -
Scheduled tasks on Windows are assigned to groups and there are multiple groups for Windows Update. As with the services, every Windows 10 computer that I checked did not have each of these scheduled tasks. Note that whatever software you use to deal with scheduled tasks, it must run as an Admin user. If not, some tasks will not be visible. (Updated Dec 8, 2018)
The Microsoft\Windows\WindowsUpdate group consists of (at most) the tasks below. All of them can be disabled normally.
And the Microsoft\Windows\UpdateOrchestrator group consists of (at most) these tasks (Updated Dec 2, 2018)
The third group Microsoft\Windows\WaaSMedic consists of a single scheduled task. I have seen it run an EXE on one machine, run as a COM handler on another machine and be missing completely on a third. (Updated Dec 2, 2018)
The fourth group Microsoft\Windows\rempl also consists of a single scheduled task that runs every day, if it exists. It may not. On a Service Pack 1803 system, it did not exist. (Updated Dec 2, 2018)
Constantinos suggests disabling only two scheduled tasks, both in the Microsoft\Windows\WindowsUpdate group: Scheduled Start and sih. He says nothing about any other Scheduled Tasks and does not address the issue of Scheduled Tasks that can not be disabled.
Some of the Scheduled Tasks that can not be disabled run at a specific time of day. I tried changing the time but could not. The Windows Security identifier (SID) that owned the task was S-1-5-18, a Local System service account whose password is none of our business. (Added Dec 8, 2018)
To block these I suggest creating an outbound firewall rule. For example, blocking program C:\WINDOWS\system32\usoclient.exe from phoning home via the firewall would neuter three scheduled tasks (Schedule Scan, Maintenance Install and AC Power Download). For more on this approach, see my later blog Killing Windows Update on Windows 10. (Updated Dec 8, 2108)
On a side note, let me recommend a great program for dealing with the Windows Task Scheduler, TaskSchedulerView by Nir Sofer. It is free, portable and from a trustworthy source. I blogged about it back in 2015.Microsoft is fighting back, which makes a full frontal assault on Windows Update that much harder. Here we clearly see how Microsoft is the enemy of anyone who wants to postpone bug fixes to Windows 10. In September 2018, Günter Born wrote about KB4023057 (Windows 10: Update KB4023057 released) which is Microsoft's latest salvo in this war. KB4023057 does a number of things to keep Windows Update chugging along. Among them, resetting network settings and modifying registry keys that get in the way. It may also repair disabled components that determine the applicability of updates. In other words, re-enable services and scheduled tasks that are involved in Windows Update. (Added Dec 1, 2018)
Clearly, these are early days for formulating a full frontal assault on Windows Update. But, the combination of continued bad patches with people who need stability more than minor fixes is likely to generate more interest. But clearly, more testing is needed. I wonder if the trick that keeps the main service disabled would be sufficient on its own? And, I wonder just blocking the five services is sufficient? This needs more testing by someone with lots of virtual machines. (Updated Dec 8, 2018)
An anonymous user at askwoody.com said they block DNS in the router. The upside to this is that it works for all PCs on the LAN. The downside is that any PC connected to a VPN bypasses the router both for DNS and any firewall rules. Then too, not many routers support this feature (my favorite router, the Pepwave Surf SOHO does support it).
The comment included the links below to Microsoft documentation on the domain names they use both for Windows Update and other Windows features:
Manage connection endpoints for Windows 10, version 1709
Windows 10, version 1709, connection endpoints for non-Enterprise editions
Manage connection endpoints for Windows 10, version 1803
Windows 10, version 1803, connection endpoints for non-Enterprise editions
Manage connection endpoints for Windows 10, version 1809
Blocking access to the outside world via DNS does not seem like a useful strategy on a single computer. DNS blocks specific URLs which the Microsoft documentation above does not always provide. For example, Windows Update uses *.hwcdn.net which can not be blocked. You can block aaa.hwcdn.net and bbb.hwcdn.net and ccc.hwcdn.net but you can not block every possible sub-domain of hwcdn.net.
Anyone who successfully blocks all updates on Windows 10 will, at some point, probably want some bug fixes. At least for bug fixes to the currently installed Service Pack, you can update manually.
I recently had a Windows 10 Home Edition machine that had not been used for a few months. It was running Service Pack 1709 with patches as of May 8, 2018 (a.k.a KB4103727 or Build 16299.431). The list of twice-a-month (roughly) patches to Service Pack 1709 is here. The page serves the same function for other Service Packs too. Reviewing the available patches, I opted to bring the system up to September 26, 2018 (a.k.a. KB4457136 or Build 16299.699).
So, I went to the Microsoft catalog and searched for KB4457136. Then, I downloaded an 870 megabyte file called
windows10.0-kb4457136-v2-x64_b4e13d384decc69a167306445a325018cd3835de.msu
and ran it. Reboot the system, as instructed, and it had the bug fixes as of the end of September.
When is it safe to install a particular clump of bug fixes? This will always be a matter of opinion. A good person to check with is Susan Bradley, also known as The Patch Lady. See maintains a Master Patch List at AskWoody.com. As I write this on Nov. 2, 2018, it is her opinion that for Service Pack 1709, it is safe to install the bug fixes released on October 9th (a.k.a. KB4462918 and Build 16299.726). She would hold off on the latest bug fixes, which were released on October 18th (a.k.a. KB4462932 and Build 16299.755).
One thing you miss this way, is the Windows Malicious Software Removal Tool (MSRT). As the name indicates, MSRT is anti-virus/anti-malware software. It is released once a month and automatically downloaded and run as part of the normal Windows Update process. You can run it manually, at any time, from a Command Prompt or the Run box by entering "mrt.exe".
There are a couple nice things about MSRT. The first is that, when you run it manually, it automatically checks to see if you have the latest version. If not, it warns you and offers a link where you can download the newer version. Even if the computer is off-line, you can easily tell which version of the software you have, the month it was released is displayed in the title bar. Also, running it manually lets you do a full scan, whereas Windows Update always seems to run a Quick scan.
So, if you avoid or disable Windows Update, you can still get and run MSRT. The latest version (as of Nov 4, 2018) is 45MB and was released on October 9, 2018. If you download it manually,the file name is a bit uglier: Windows-KB890830-x64-V5.65.exe.
Another thing to manually update is Windows Update itself. Microsoft publishes links to the latest version of it here: Latest Servicing Stack Updates. In their world, Windows Update is a Servicing Stack. The Dec 7, 2018 Servicing Stack Update for Windows 10 Service Pack 1709 is KB4477136 and for Service Pack 1803 it is KB4477137. Hat tip to AskWoody.com. (Updated Dec 11, 2018)
Then too, there is the Adobe Flash Player which is updated on its own. That is, it is not included in with other Windows patches. To get the latest Flash update, start at the Microsoft Catalog, search for "Flash" and sort the results by the Last Updated column. A single Flash update will appear in the catalog many times, find the one that exactly matches your system. The download and installation process is fairly straight forward. There are many reasons to avoid Flash, but I can think of no reason not to have the latest version of Flash installed.(Added Dec 7, 2018)
Still more software that has its own patches, separate and distinct from Windows patches, is the .NET Framework. See NET Framework December 2018 Security and Quality Rollup for links to get the Dec 2018 patches from the Microsoft Update Catalog. (Added Dec 11, 2018)
Drivers too, can be updated manually. In fact, for many years this was a standard recommendation. One approach is to use software from the hardware manufacturer of the computer. Many PC companies pre-install software that updates both drivers and any of the other software they may have pre-installed. If you are only interested in the driver for one specific piece of hardware, then go to the website of the company that made the hardware in question. (Added Nov 6, 2018)
On October 7, 2018, Martin Brinkmann of gHacks.net wrote about a change in the way Windows 10 installs printer drivers. As with everything Microsoft touches, it is getting worse. Prior to Service Pack 1809, Windows included basic drivers for printers and it would install these drivers automatically so that printers could work right away. Starting with Service Pack 1809, Windows no longer includes most of the basic printer drivers. For a printer to work immediately, on a PC that shipped with 1809, requires the use of Windows Update to download drivers. So, anyone who blocks Windows Update has to do things the old way, finding, downloading and installing drivers from the website of the printer manufacturer. (Added Nov 6, 2018)
An AskWoody.com user (dhdoyle) has another approach for manual updates: run Belarc Advisor to see the missing updates, and use Belarc's links to download the individual updates and then manually install them. I have not tried this. (Added Dec 11, 2018)
As for new Service Packs (aka Feature Updates), Martin Brinkmann (October 2018) wrote about three ways to manually download it. The best option is the Microsoft Media Creation Tool which can both update the machine it is run on, or, create installation media (USB flash drive, DVD, or ISO file). You can double click on the ISO file and run setup.exe. Or, you can boot off the USB flash drive or DVD to install the Service Pack. In addition to upgrade installations, the USB flash drive and DVD can be used to perform a clean installation too (which wipes out everything as its first step). Added Dec 18, 2018
Is this too much? Am I over-reacting to the danger of just-released bug fixes?
Let's not forget that Windows Update even fails at updating itself.
I oversee a number of Windows 7 machines. More than once I have updated a PC with the August 2018 or September 2018 monthly patches only to run Windows Update again, after the last patch was installed and the system rebooted, and find that it wants to install a patch that was first released back in September 2016. This missing patch is to Windows Update itself and without it many people experienced a 0x8000FFF error. Then, when Microsoft tried to fix this, they screwed that up too. And, back to euphemisms, rather than fixing a bug in Windows Update (shell shock), Microsoft released a Servicing Stack Update (Post Traumatic Stress Disorder).
Susan Bradley has been on the front lines of this fight, well before the bad publicity generated by the assorted problems this month. She wrote an open letter to Microsoft on July 30, 2018 which was published by Woody Leonhard in Computerworld: An open letter to Microsoft management re: Windows updating. This was also covered on Aug. 7th by Gregg Keizer: Patch expert calls on Microsoft execs to fix Windows updating. Bradley circulated a questionnaire among business IT administrators, specifically the people responsible for patching Windows systems. Even back in June and July, they were not happy with either the process or the quality of updates. They complained that the Insider program, which should find bugs, does not work well and too many bugs are released to the public. This same point was made by Peter Bright on October 20th (see below). Roughly 80% said that Windows 10 Service Packs were not useful and that they should be released either once a year or every other year. And, the bugs extend to documentation. Quoting: " Starting in January of this year with the release of Spectre/Meltdown patches, there have been numerous instances where patching communication has been wrong, registry entries detailed in Knowledge Base articles regarding registry key application was initially incorrect..." Bradley is an expert on Windows patching and cited many specific examples of screw-ups. The response from Microsoft was a virtual, "go away kid, don't bother me." However, a few months later, big corporations were allowed to postpone the installation of Windows 10 Service Packs. This delay does not apply to Home and Professional Editions. (Added Oct 26, 2018)
Mary Jo Foley has covered Microsoft for ZDNet for years. She clearly has her ear to the ground. What does she, herself, do? On October 10th, she wrote:
"Even after the first two or three or four cumulative updates roll out for a new feature update, I am still leery about putting it on my PC. I know these releases have gone through testing internally at Microsoft and externally through the Insider program, but they still inevitably cause various compatibility and other issues for users right out of the gate. And I just don't have the time, or in many/most cases, the knowledge, to fix what breaks."
Translating: The term "cumulative update" refers to the twice-a-month bug fixes to a Service Pack. A "feature update" is a Service Pack. In essence she is warning us to be wary of new Service Packs and wait as long as possible before installing them.
And, after I thought I was finished writing this article, along came Gregg Keizer in Computerworld with Critics warn Microsoft it needs to fix broken update process. Keizer writes that "Calls for Microsoft to improve the quality of its upgrades and updates have been building for some time" and notes that many people attribute Microsoft's 2014 dismissal of internal testers to the decline in quality. Along those lines is the latest Windows Update disaster, the installation of the 1809 Service Pack deleting users' files. The bug was reported to Microsoft, and ignored. It was such a disaster, that Microsoft stopped the rollout of the 1809 Service Pack.
Here are some points made by experts in the article.
On October 10th, Windows expert Ed Bott aired his gripes in Two Windows 10 feature updates a year is too many (I read this after writing this article). He writes "For at least the past year, I've been hearing loud protests from the IT pro community and other Windows support professionals over the number, the pace, and especially the quality of Windows updates ... the Windows 10 upgrade cycle has been unnecessarily disruptive, especially to home users who don't have the technical skills to deal with those updates ... Feature updates ... because they are full Windows upgrades, they take much longer to install, especially on well-worn budget PCs. More importantly, each such update introduces a new set of possible compatibility and reliability problems. For the people trying to get work done with a Windows 10 PC, each new feature update is an unwelcome disruption." (Added Oct 21, 2018)
Five days later, Bott piled on, griping about Microsoft using untrained volunteers as beta testers. He quoted a Microsoft employee complaining about the flood of moronic bug reports that make it hard to find real problems. He argues that Microsoft needs to have professional software testers, writing "The two most serious bugs in this cycle ... were caused because of a change in the fundamental working of a feature. An experienced software tester could have and should have caught those issues. A good tester knows that testing edge cases matters. A developer rushing to check in code to meet a semi-annual ship deadline is almost certainly not going to test every one of those cases and might not even consider the possibility that customers will use that feature in an unintended way." (Added Oct 29, 2018)
Yet, his fellow ZDNet reporter, Mary Jo Foley wrote: "Speaking of testing, it's widely known that Microsoft let go a bunch of its Windows testers back in 2014, substituting flighting and new unit testing procedures in their stead. I don't think Microsoft will reverse this course and bring back testing as a separate discipline." (Added Oct 29, 2018)
On October 3rd, Windows expert Woody Leonhard wrote How to block the Windows 10 October 2018 Update, version 1809, from installing, which I also read after initially writing this article. In it Woody says: "As we've seen, repeatedly, upgrading to a new version of Windows 10 as soon as it's out leads to madness ... For almost everyone, the new features in Windows 10 version 1809, a.k.a. the October 2018 Update ... just aren't worth the bother of installing and setting up an entirely new copy of Windows. (Unless you really want Candy Crush Soda Saga installed for the umpteenth time)" There are links and references to this article scattered above. (Added Oct 21, 2018)
And, the hits keep coming ... Peter Bright of Ars Technica, just today (Oct. 20th), wrote Microsoft’s problem isn’t how often it updates Windows—it’s how it develops it. Ouch, this article is pretty damning. To understand the quotes from the article below, be aware that the term "Windows as a Service" is doublespeak for issuing two Windows 10 Service Packs each year. Here are, to me, the best parts of this long article. (Added Oct 21, 2018)
Today, another griper: Windows 10 'as a service': Broken by design? by Günter Born. The 1809 Service Pack of Windows 10 has been withdrawn by Microsoft, yet on this page Windows 10 release information it is marked as Recommended. The article is in German but Chrome translates it just fine. (Added Oct 22, 2018)
When your big fans turn against you, that's bad. Leo Notenboom wrote Microsoft, We Deserve Better on Oct. 24, 2018. Quoting: "In recent weeks, I’ve seen calls from several sources suggesting that Microsoft stop, take a breath, and seriously review their update process. I agree. This madness must end ... I still believe that most people should take all updates, albeit with extra attention to backing up first ... [but] since updates are forced, it’s a little like playing Russian Roulette. There's no real predicting whether or not the barrel is loaded when you’re forced to pull the Windows Update trigger ... Even if your chances of experiencing a problem are one in ten thousand (aka 0.01%), it’s certainly enough to make people nervous." Rather than just griping, Notenboom offers excellent suggestions for Microsoft.
"Allow all editions of Windows to defer any and all updates indefinitely. Honestly, it’s the height of hubris for an operating system to force updates to begin with. There are hundreds of reasons why an individual machine might not or should not take updates for an extended period of time. Stability matters, and right now, given the risk that updates appear to present, stability matters more than security (the most quoted reason for automatic, unstoppable updates). Let all computer users choose if, when, and which updates should be installed. Period. Sure, make the default action 'take everything automatically', but give everyone an out. You don’t know their reasons, you can’t know their reasons, and there are valid reasons. Encourage, educate, and build a track record of trust. But never force. "
To this, I say YES YES YES. A thousand times, YES. (Added Oct 25, 2018)
On November 8, 2018 we heard about Office 365 being installed on a computer in London’s Victoria train station that is used to display train delays. The notice about the software installation blocked a big part of the screen (see it) - no train information for you. This stems from the Microsoft mind set, that they are in charge, not you.
Finally, back to patch expert Susan Bradley. In her plea to Microsoft, back in July, she wrote that "Some are disabling Windows Update as a drastic measure to ensure that updates do not reboot systems when they are not wanted."
So, no, I do not think the advice in this article is an over-reaction.
The big question is at what point do we spend too much time on the care and feeding of our operating system? At some point, our time would be better spent doing productive work, or even just goofing off, with a system that does not require so much work to defend and maintain.
Large companies have herds of nerds to babysit Windows. Fine. Outside of large companies, I don't think anyone should use Windows. Certainly, non techies should not use Windows. It is clearly the worst choice among the currently popular OSs (macOS, iOS, Linux, Android). Just to cite one issue, on three of the other four systems, there is no such thing as anti-virus software.
To me, it is clear that Microsoft both develops and tests Windows using flawed procedures. Almost universally, Windows 8 was considered a step backward from Windows 7. Likewise, many techies want no part of Windows 10. It feels like Microsoft keeps making things worse. Opinions aside, the operating system is huge, bloated and very very old.
Windows will survive for years due to the large amount of software that only runs on Windows. In addition, techies in large companies have no interest in seeing those companies convert to a different system, one that they are not familiar with. Anyone who does not need software that is married to Windows, is better off using a different operating system.
FYI: Office functions much like Windows 10. Ugh. (Added Nov 20, 2018)
By the way, Chromebooks also force Operating System updates on users, but I have yet to hear of an update to ChromeOS causing the type of problems that updates to Windows cause. And, no one has ever spent hours watching a Chromebook update itself with a new version of the operating system.
| | ||
| @defensivecomput | TOP | Home => Defending against Windows 10 bug fixes |
| michael--at--michaelhorowitz.com | Last Updated: October 11, 2019 5 PM | ||

Copyright 2001-2024 |
Copyright 2001-2024 |