| Michael Horowitz |
Home => Web browser fingerprinting - testing the testers
|
| Michael Horowitz |
Home => Web browser fingerprinting - testing the testers
|
| [Formatted for Printing] | From the personal web site of Michael Horowitz |
November 27, 2019
Anyone concerned with being tracked on-line needs to be familiar with web browser fingerprinting. Without using cookies, fingerprinting can convert the web browser on a computer into a unique identifier by which your actions can be tracked. Last month, Geoffrey A. Fowler wrote about it in the Washington Post: Think you're anonymous online? A third of popular websites are fingerprinting you.
Browser fingerprinting is done by looking at many, seemingly trivial, aspects of a computer and web browser and combining all that information into a profile. Most of the time, these profiles turn out to be unique. Some attributes that are examined are: the computer operating system, the time zone it is in, the language the computer is using, how much RAM the computer has, the screen height and width, the browser being used, the fonts and plug-ins that are installed, the audio and video formats that are supported by the browser, and much more.
It is very hard to defend against browser fingerprinting. Private browsing mode, for example, is not a defense. Neither is a VPN or the Tor network. Blocking cookies also does nothing.
There is no one way to make a browser fingerprint. Each one is a combination of dozens of pieces of information. Regardless of the specific formula however, the critical issue is whether a given fingerprint is unique or not.
I recently added a section on browser fingerprinting to my DefensiveComputingChecklist.com web site. After writing up this summary of the topic, it occurred to me to test the two fingerprinting "tester" websites, amiunique.org and panopticlick.eff.org.
How can you tell if the tester websites are doing what they are supposed to be doing? By presenting them with the exact same data multiple times. Not knowing the formula, this poses a problem.
Still, a Chromebook running in Guest Mode should provide the same profile every time. Guest Mode is one of the best things about a Chromebook. It starts out, every time, with a virgin copy of the ChromeOS system. There are no favorites, no browser extensions and no other software besides the Chrome browser. When you log out of Guest Mode, everything is wiped out. You can think of it as private browsing mode on a just-installed copy of a web browser.
The profile of the Chrome browser on any one specific Chromebook should not change until the operating system itself is updated. The same effect could also be had using virtual machine software that supports checkpoints. You could run a fingerprint test and then rollback the virtual machine to the last checkpoint and run another test. I tested with a Chromebook.
Over and over, I would run a test at each of these two sites, then Exit out of Guest Mode and go back in to Guest Mode. If the sites do what they claim, they should see these Guest mode sessions as the same. It did not go well.
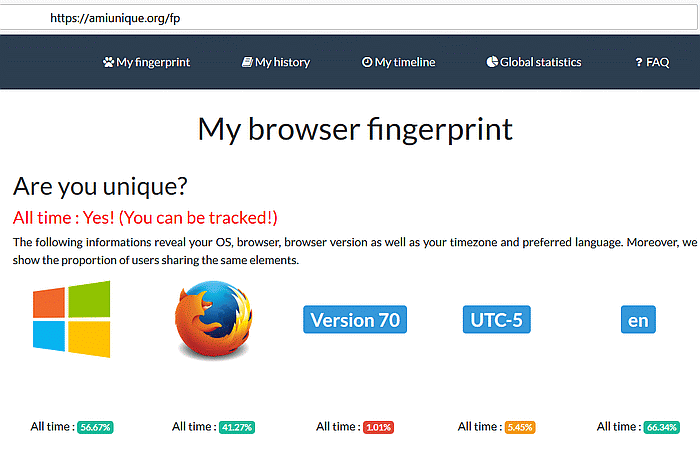
AMIUNIQUE.ORG
At amiunique.org, the Guest Mode copy of Chrome was said to be unique every time. I call foul. I doubt this can be true.
At the time I was testing, the site had collected roughly 1,425,500 browser fingerprints.
There are some other reasons to be suspicious of the site. The home page features a heading of "newVersionTitle" which makes me wonder if it has been abandoned. Also, the site offers extensions for Chrome and Firefox that track the browser fingerprint. The Chrome extension was last updated in October 2015. The Firefox extension was last updated in October 2017. Looks abandoned.
Who created the website? It does not say, it only says where it is hosted.
The reported data can be useful, and it's presented in a very easily understood format, but I have doubts about the final conclusion about uniqueness.
I emailed to the address on the home page, and someone responded quickly. The site has not been abandoned. The heading on the home page was fixed in a day. They were also very interested in my test results.
To help them in debugging, I have posted here the results of two tests, done a minute apart, each on a Chromebook in Guest Mode. I simply printed the web page to a PDF. Test 1 and Test 2. Looking at them side by side, I see that some data got cut off in each test. Sometimes data at the bottom of a page is simply missing. For example, the first JavaScript attribute was chopped off in one PDF. So, not the best debugging approach.
I found it interesting that the web browser self-identifying string (User Agent) was seen less at 0.01% of the time. Clearly, not many people are testing with Chromebooks. The User Agent was:
Mozilla/5.0 (X11; CrOS x86_64 12499.66.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.106 Safari/537.36
Also of interest was the Battery level. If this is part of a fingerprint, it means that devices using a battery can not be tracked long term as their battery level would constantly change. I doubt that advertisers include the Battery level in their fingerprints.
My best guess for why each Guest Mode Chromebook session appears to have a unique fingerprint is something called "media devices". I don't know what "media devices" are, but it seems that the Chromebook generates a unique value for this every time.
As I write this on November 27, 2019 the people behind amiunique.org are looking into this issue. If I hear back, which I expect to, I will update this blog.
PANOPTICLICK
Panopticlick is a service from the Electronic Frontier Foundation (EFF) that dates back to 2010.
In the first test, it reported that "Your browser has a nearly-unique fingerprint". The detailed results said that one other computer/browser had the same fingerprint. This may have been from a prior test I did a few days earlier.
However, the 2nd, 3rd and 4th tests also reported that there was 1 other computer/browser with the same fingerprint. Still more tests failed to increase the tally beyond 1. This is either a bug or a bad explanation of what the number represents. The exact message is:
"Within our dataset of several hundred thousand visitors tested in the past 45 days, only one in 126693.5 browsers have the same fingerprint as yours."
There were two other minor issues too.
The number of browsers in their database changed, drastically, every time. Some numbers that I saw just minutes apart were: 252,750 and 84,236 and 126,399.
The last bug is evident in the quote above. How is the number of browsers not an integer? Some other numbers I saw in my testing were: 63,241.25, 50,609.2, 42,177.0 and 36,154.14.
I emailed the EFF and heard back quickly. What have here, is a failure to communicate. They claimed it was not a bug, just a poor explanation of the situation. They said that each instance of the Guest Mode Chromebook was indeed generating the same fingerprint. I could not, however, understand their emailed second explanation of exactly what the site is trying to convey. However, that the numbers above are decreasing from (roughly) 63,000 to 50,000 to 42,000 to 36,000 can be taken as an indicator that my fingerprint has been seen more often.
They realize they need to improve their explanation. If they do, I will update this blog.
SO WHAT?
Without a reliable tester website, there is no way to insure that our defenses against browser fingerprinting are working. And, since defending is so hard, we really need this. The one exception that I know of is the Brave browser (only tested on Windows) which reports when it has blocked a fingerprinting attempt (see a screen shot).
Thanks to the amiuniuque.org website, I found three other fingerprint tester websites. However, each failed.
- - - - -
Leave a comment by replying to this tweet.
| | ||
| @defensivecomput | TOP | Home => Web browser fingerprinting - testing the testers |
| michael--at--michaelhorowitz.com | Last Updated: December 31, 2019 9PM UTC | ||

Copyright 2001-2024 |
Copyright 2001-2024 |