| Michael Horowitz |
Home => Why I like my router
|
| Michael Horowitz |
Home => Why I like my router
|
| [Formatted for Printing] | From the personal web site of Michael Horowitz |
April 26, 2019
These articles (here and here), about a couple million insecure hackable IoT devices, made me realize, again, why I like my Pepwave Surf SOHO router.
For one thing, if I suspect an IoT device, I can easily log all outbound connections the thing makes. The resulting log entries appear in the Event Log of the router, no extra software or servers needed. Looking at it differently, I can also log suspicious traffic from any device to see if I have a device that uses the vulnerable protocol discussed in the two articles.
An example of this logging, done with an outbound firewall rule, is shown below.
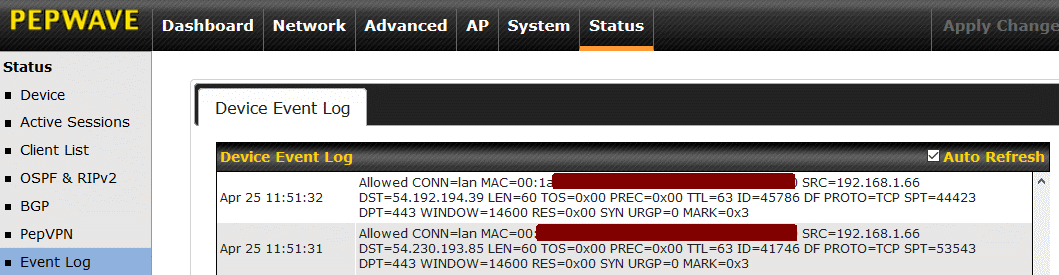
The log shows a device at IP address 192.168.1.66 (SRC field) making two outbound connections. The destination IP address is identified as DST in the log entry. Here we see outgoing connections were made to computers at IP address 54.192.194.39 and 54.230.193.85. Each connection used TCP, not UDP (from the PROTO field) and each had a destination port (DPT) of 443, showing the connection was encrypted.
Yes, just knowing the outbound IP address is somewhat limiting, but its not to hard to get a domain name from an IP address.
The particular vulnerabilities discussed in the two articles can be prevented by blocking outbound UDP requests to port 32100. Can your router do this? Mine can, easily, with an outbound firewall rule as shown below.
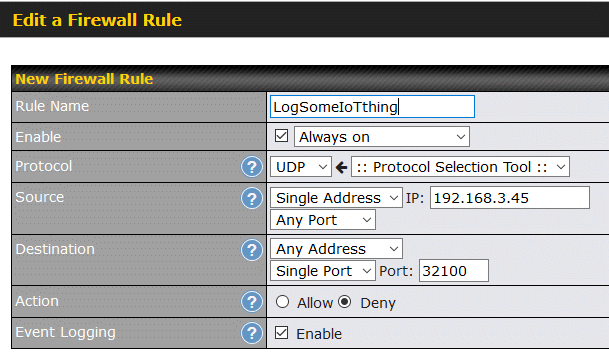
When a rule is used for logging, the Action is Allow, when used for blocking, the Action is Deny. In the first screen shot above (the Event Log), the first word of each log entry is "Allowed". An outbound firewall rule can block just one device from using this UDP port or it can block all devices (Source fields). In the example above, it is blocking just the device at IP address 192.168.3.45. We could have blocked outbound UDP port 32100 requests on all devices, by specifying a Source of "Any Address" In addition to controlling UDP, Peplink routers can also control the TCP, ICMP, DSCP and IP protocols.
The outgoing Destination in this case is a single UDP port, number 32100. Other supported destinations are a single IP address, an entire network or a domain name. The point being, there is lots of flexibility.
To deal with the particular issue raised in these two articles, all I need to do is block outbound connections on UDP port 32100 from any device connected to the router. And, I have. For good luck, I enabled logging of the firewall rule, so I can tell if a vulnerable device ever gets on my network.
The router offers other defensive tactics too.
I can put suspect devices into a VLAN (more here), an arbitrary group of devices connected to the router. The router supports two types of VLANs: one allows the segregated devices to see each other and one does not. VLANs can be assigned to LAN ports and/or wireless networks. It is common to give a VLAN its own wireless network, as the router can create up to 16 SSIDs. Even ignoring IoT, a VLAN can keep devices used by children isolated from those used by adults, or, devices used for personal stuff from those used for work. Again, lots of flexibility.
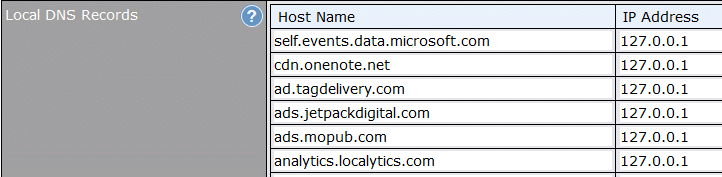
We all know that Windows 10 spies on us, and the Surf SOHO offers protection here too. Take, for example, two domains that Microsoft uses for Windows 10 and Office: self.events.data.microsoft.com and cdn.onenote.net. I can block these domain names with DNS.
To begin with, I can force all devices connected to the Surf SOHO to use the router as their DNS servers. Not many routers can do this. Then, I can specify individual DNS entries in the router. Using that feature, I can assign a domain name to the IP address 127.0.0.1. This IP address is special, in that it always refers to your computer. The feature is called Local DNS records and, as shown below, it can also be used to block some ads and analytics. Techies can think of this as the hosts file on steroids.
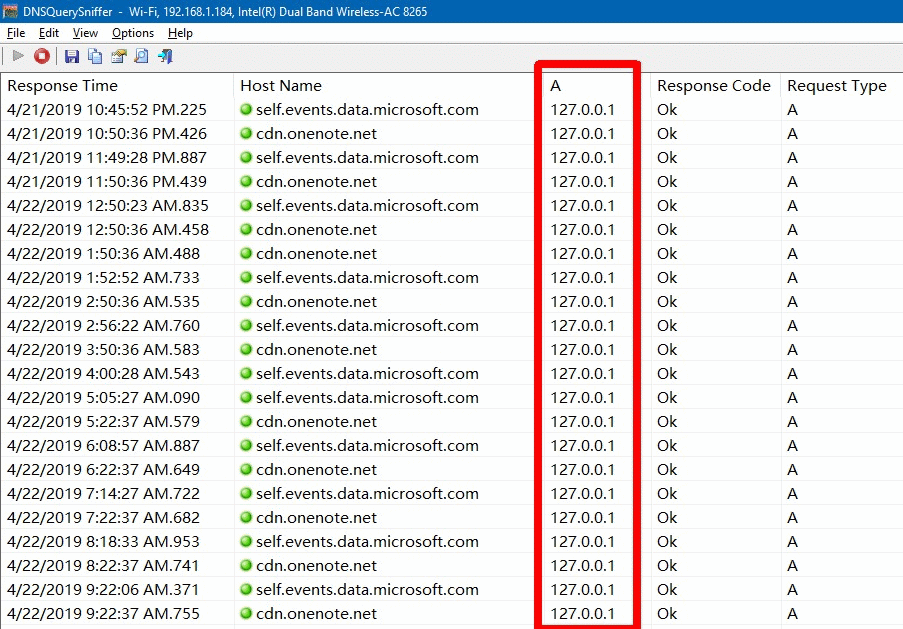
In the case of Windows 10, assigning these two domain names to 127.0.0.1 means that no computer on my network, Windows or not, will ever make an outgoing connection to them. You can see this in action below, which shows a log of DNS calls on a Windows 10 machine. Every time Windows made a DNS request for the IP address of these two domains, it was told 127.0.0.1. Take that Microsoft.
These features are not limited to the Pepwave Surf SOHO, they also exist on higher end Peplink routers. The Surf SOHO is just their cheapest router.
Insecure IoT doesn't scare me. Should it scare you? Depends on your router.
| | ||
| @defensivecomput | TOP | Home => Why I like my router |
| michael--at--michaelhorowitz.com | Last Updated: July 4, 2022 8 PM | ||

Copyright 2001-2024 |
Copyright 2001-2024 |