The image below comes from my JavaTester.org website and is included securely. Specifically, the HTML code that fetches the image
into this page is
< img src = "HTTPS://javatester.org/pix/CastleWilliams.and.NJ.jpg" / >
Does your web browser warn you about data included from an outside source? Probably not. The attitude, as a rule, is that as long as everything is fetched via HTTPS, its all good.

Images are the best case, as they are not executable code. However, including executable JavaScript is the normal mode of operation for many, if not most websites. For example, consider the home page of CNN.com. The image below was from their home page on Feb. 20, 2018 viewed with Firefox 58.0.2. After loading the page, I clicked on Tools => Web Developer -> Network.
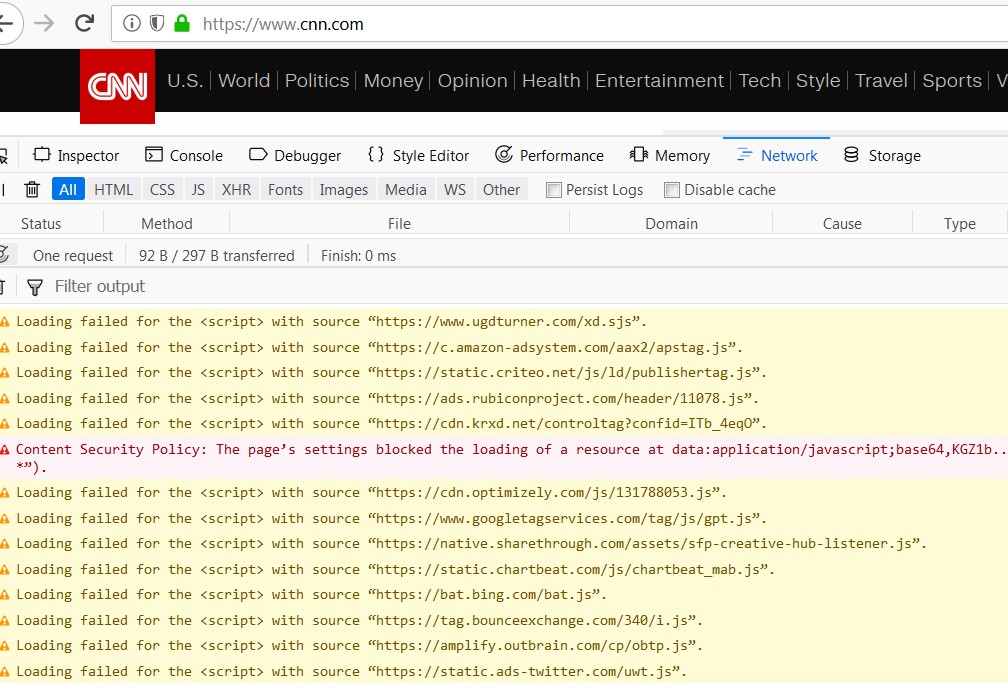
This clearly shows that the CNN home page includes scripts from many other sources. They failed to load, I'm sure, thanks to the adblocker installed into Firefox.
Not to pick on CNN or be limited to Firefox, the image below shows the CNET home page viewed in Chrome with no ad blocking. After the page loaded, I clicked on the three vertical dots, then More Tools -> Developer Tools -> Network. This clearly shows that it tried to load JavaScript code from z.moatads.com and tps30.doubleverify.com.

In both the CNN and CNET examples, we are only seeing the off-site includes that failed to load. The list of those that succeeded is much larger.
iframes are another variation on this theme, see iframes.html.
The next page in this series, InsecureImage.html offers another wrinkle.