| Michael Horowitz |
Home => Routers can force their DNS servers onto all devices
|
| Michael Horowitz |
Home => Routers can force their DNS servers onto all devices
|
| [Formatted for Printing] | From the personal web site of Michael Horowitz |
March 5, 2018
On the February 20, 2018 edition of Steve Gibson's Security Now podcast, someone asked about which DNS servers get used when a computer has hard coded DNS servers that are different from those in the router. Gibson responded that the DNS servers in the computer were used. As a long-time Peplink router user, I knew that this was not necessarily the case with Peplink routers.
After the show on the 20th, I wrote Steve the following note, which he read on the February 27th show:
"Peplink routers can over-ride all DNS requests from devices connected to their routers. In this case you WILL use the DNS servers in the router, *not* those hard coded in your computer. From the perspective of router, its easy, just look for outgoing port 53 traffic."
This resulted in a five minute discussion between Steve and show host Leo Laporte centered on two instances where a computer can answer a DNS query on its own and not need to make a request that the router sees. In one case, a recently resolved DNS query (say grc.com -> 4.79.142.200) will be cached by the computer. The other exception is the hosts file. Domain name to IP address associations in the host file seem to be checked before anything else.
You can read the transcript of the show (search for my name) or listen to the 5 minute conversation at SoundCloud.com.
SO WHAT?
So what, you ask? There are good reasons, both at home and when using public Wi-Fi away from home, to be aware of a router that can force the use of its configured DNS servers.
At home, good DNS servers can provide some extra security and protection. Some block malware and phishing websites (OpenDNS and Quad9 come to mind). Not only might this prevent a malware infection, it may also help afterwards - a malware infested machine might be prevented from phoning home to its master control servers. Also, you can get some typo protection from DNS servers, so that you don't land on a malicious website. And, DNS servers can also block pornography, hate oriented websites and assorted other topics. Good DNS servers are an integral part to Defensive Computing.
When traveling or using public Wi-Fi, the situation is reversed. Here, a computer that is configured to use better/safer DNS servers, may find that the router running the public wireless network has forced bad DNS servers upon it. How would you know? There are many websites that tell you which DNS servers your computer is ultimately using. A partial list is on the Test Your Router page at my RouterSecurity.org site.
The best, but not only, way to avoid the DNS servers at a public Wi-Fi network is to use a VPN. By encrypting all data to/from the Internet, the VPN prevents the router from seeing DNS requests.
And, there is still more to the story.
For one thing, there is the basic question of whether the router is serving as the DNS resolver for devices attached to it, or whether the router does nothing but pass DNS requests out the Internet. The discussion on the show, did not consider that the router might be acting as the DNS server. If a computer shows two public IP addresses as its DNS servers, then the router is merely acting as a middleman. However, if a computer shows the LAN side IP address of the router as its sole DNS server, then the router is acting as a DNS server.
Even if the router is functioning as a DNS server, it still has to pass along many, if not most, requests to other DNS servers. Again, to see which DNS servers your computer is ultimately using, see my Test Your Router page.
As for Peplink routers, including the Pepwave Surf SOHO that I recommend, the feature that instructs the router to impose its will (its DNS servers) on all attached devices is called DNS Forwarding and, as shown below, it is enabled with a simple checkbox.

Note in the description, it says that DNS lookups will be "intercepted and redirected to the built-in DNS name server." This means that before a Peplink router can force clients to use its DNS servers, it must first be configured to act as the DNS server. When the router is acting as the DNS server, DHCP clients will see the LAN side IP address of the router (192.168.50.1 by default) as their DNS server. This is true with or without DNS Forwarding being enabled.
To be clear, when DNS Forwarding is being used, all devices, even those with hard coded IP addresses and hard coded DNS servers, will bow to the will of the router. The router will honor the hard coded LAN side IP address, but not the DNS servers. The client device will think it is using its desired DNS servers, but it won't be. You can use the many DNS tester websites to verify this.
Peplink is not unique in offering the ability to over-ride user specified DNS servers. As a rule, this is a feature of business class routers.
Steve Gibson himself uses pfSense, and it too, can enforce its will when it comes to DNS servers as shown in two articles below.
Redirecting all DNS Requests to pfSense
Quoting: "To restrict client DNS to only the specific servers configured on a firewall, a port forward may be used to capture all DNS requests sent to other servers. Before adding this rule, ensure the DNS Forwarder or DNS Resolver is configured to bind and answer queries on Localhost, or All interfaces. "
Blocking DNS queries to external resolvers
Quoting: "This procedure will allow the firewall to block DNS requests to servers that are off this network. This can force DNS requests from local clients to use the DNS Forwarder or Resolver on pfSense for resolution. When combined with OpenDNS, this allows DNS-based content filtering to be enforced on the local network. Certain local PCs could be allowed to use other DNS servers by placing a pass rule for them above the block rule."
This is also something that OpenDNS would prefer people use and to that end they wrote How to prevent users from circumventing OpenDNS using firewall rules which says: "Savvy internet users may try to bypass OpenDNS services if your network security configuration allows them to change the local DNS IP server address to something other than the addresses of our public servers .... However, it is possible to not allow those other DNS services through your network firewall to the Internet, which will prevent these users from circumventing the protection."
The suggestion offered by OpenDNS is not specific to any one router, just to use a couple firewall rules. This is the same technique used by pfSense. To me, configuring a Peplink router is easier.
Later in the Security Now show, a chatroom user reported that the Ubiquiti EdgeRouter X can also force DNS servers on all clients.
AND MORE
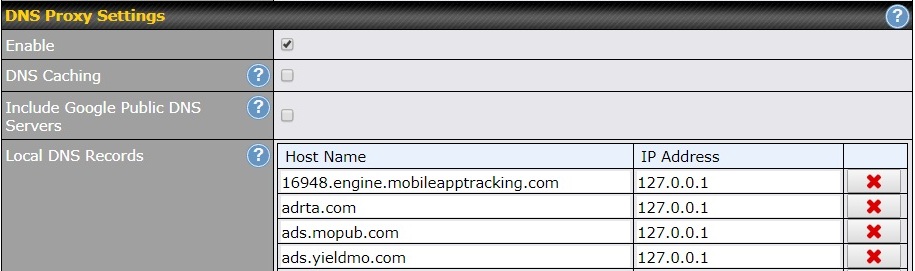
Configuring a Peplink router as the DNS server for client devices has another advantage - you get to configure Local DNS records as shown below. This gives you the ability to block websites and domains. In the four examples below, each domain (Host Name column) is assigned to IP address 127.0.0.1. This is a reserved IP address that always refers to your computer. Making this assignment insures that these domains will never load on any computer connected to the router.
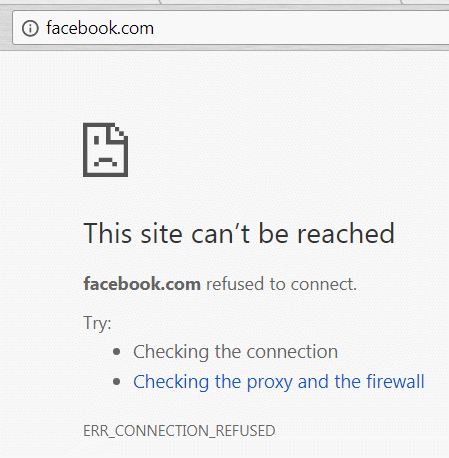
To see this in action, the below is what happens in the Chrome browser when facebook.com is assigned to 127.0.0.1 in the Local DNS records list above.
If this sounds like the hosts file, it is the same concept. The difference being that a hosts file applies only to the computer it resides on, whereas, using the router, the effect applies to all devices connected to the router.
OK, perhaps not all devices all the time. As noted above, a VPN should bypass the DNS servers in the router. I have not tested this, but Tor should too. And, the hosts file on a computer is normally checked before anything else, so entries there would prevent the computer from any DNS interaction with either the router or the Internet.
Update: March 20, 2018: Finally, I am told that a couple Windows anti-virus programs have their own take on DNS in an attempt to secure it. AVG has a SecureDNS feature that uses port 443. Webroot offers a DNS feature that uses port 7777. I have not tested them, but you would expect both services not to be affected by any router.
Update: August 12, 2018: According to this article, D-Link Router Configuration Supplement - DNS Relay, D-Link routers can also serve as the DNS server regardless of how client devices are configured. They call it "DNS Relay" and the feature needs to be disabled to use OpenDNS.
| | ||
| @defensivecomput | TOP | Home => Routers can force their DNS servers onto all devices |
| michael--at--michaelhorowitz.com | Last Updated: August 12, 2018 6 PM | ||

Copyright 2001-2024 |
Copyright 2001-2024 |