| Michael Horowitz |
Home => The BEST password advice
|
| Michael Horowitz |
Home => The BEST password advice
|
| [Formatted for Printing] | From the personal web site of Michael Horowitz |
2024 updates: June 3
2023 updates: Nov 2, 1 | Oct 26, 24, 22, 20, 12 | May 31, 26, 18, 4 | March 16, 5 | Feb 12, 11, 8 | Jan 9, 8, 7, 5, 3, 2
2022 updates: Dec 2 | Oct 17 | Aug 27, 25, 19, 3 | July 26 | Feb 25, 19, 13 | Jan 4
2021 updates: Nov 17 | Sept. 13, 3 | June 10 | May 25 | April 24 | March 31, 11, 10 | February 21, 28 | January 19
2020 updates: November 29, 21 | October 25, 24, 19 | September 18 | July 30, 25 | April | March | February
Created: August 16, 2019
INTRODUCTION (last updated June 3, 2024)
Seeing as how it is 2019 2024, you might think that everything there is to say about passwords has already been said. But, no. Heck, I updated this page with two
new sections in February of 2022 and another new section in January 2023.
The blog title is purposely exaggerated. The best password advice is that which improves your current system/approach, and it will be different for everyone. Every approach to generating, storing and retrieving passwords has its pros/cons. If you stop reading here, just note that anyone who pushes a particular approach without a serious discussion of the downside, is not worth listening to.
Most password advice is flawed. Some advice is intended to help people pick a single "good" password when we all need hundreds of passwords. Other advice comes from techies thinking in the box and is only appropriate for other techies. The newest section here was prompted by the story of a techie whose passwords were too secure. Some advice sells the fantasy that you can have both ease of use and increased security. And far too much advice comes from people devoted to the one true solution, who ignore other approaches.
We all need hundreds of passwords that need to created, stored and retrieved. When creating them, they need to be reasonably long and reasonably unique. Advice that is solely focused on storage/retrieval is not addressing the entire problem.
Long passwords (12 characters is probably a minimum length, the exact number is debatable) defeat brute force guessing attacks. Wi-Fi passwords are one case where bad guys can make billions of guesses a second for as long as they care to. The password "TipTop9!" has upper and lower case letters, a number and a special character, so it looks good when judged by the common yardstick. But, it will not stand up to a brute force attack for very long.
Unique passwords defeat two other types of attacks. In one, bad guys try to guess your password using lists of popular passwords and/or lists of previously stolen passwords. Even if a password is not globally unique, it is far better for it be so rarely used that it never appears on any list of the most popular passwords. In the other attack, bad guys use a password of yours, stolen from one website, at many other websites, hoping that you re-used it. The common terms for this are "password stuffing" or "credential stuffing".
While reasonable people can dis-agree on the best approach to passwords, one thing all techies agree on is to never re-use a password. When one password is compromised, we want to limit the damage. Especially, we do not want the password for an un-important website/system to provide access to an important site/system. But, we all have so so many passwords for things that we don't care about at all. I get it. It's tempting to re-use a single password for these accounts. A password formula, as explained below, is a much better solution while also being easy to use.
As an aside, let me note that password stuffing depends on using the same userid/email address at multiple websites. So, don't do that. If you are offered the chance to login to a new system using an existing Google or Facebook account, don't do it. If you get to chose a userid, choose a new one every time. If a system/website uses an email address as the userid, then it is best to have hundreds of available email addresses. There are many ways to funnel multiple email addresses into a single mailbox. For more on that, see the email topic on my DefensiveComputingChecklist.com website.
There are multiple solutions for dealing with hundreds of passwords. Perhaps the most popular approaches are:
Three of these solutions simply help retrieving passwords, they do nothing about making them long or unique.
I wrote this blog initially to make the case for using a formula. But again, we all have different needs and abilities so there is no one best solution for everyone. Even for a single person, the best solution may be to use different approaches for different passwords. Experience has shown that email and financial passwords deserve special attention. For Apple customers their AppleID password falls in this category too.
Gabriel Fair is a case in point. He has 5 different types of passwords and deals with each type differently. He may have over-analyzed, but using one system for all your passwords is likely to be just as extreme and sub-optimal.
FYI: If using an encrypted Word document or Excel spreadsheet appeals to you, the concept can be expanded using VeraCrypt. VeraCrypt is free software that runs on Windows, macOS, Linux and the Raspberry Pi. It can create an encrypted volume/blob that is protected with a password that acts much like the Master Password for Password Manager software. It replaced TrueCrypt. On Windows, the volume is a drive letter. While a volume normally contains many files, you control the size and it can be very small. You can create a plain text file as the only file in the volume and store your passwords there. A volume remains unlocked until you manually lock it (dis-mount is the term the software uses). There is no official version for iOS or Android but unofficially there is. (Added May 4, 2023)
NOTE: Password managers can store more than just passwords. While the rest of this page is about storing passwords, on my DefensiveComputingChecklist.com site, I make a case for using a password manager to store photographs of important documents. See the Traveling topic.
PAPER HAS ITS PLACE top
The main purpose of this blog is introduce Formulas as a better alternative to password managers. There is a section below with my arguments against password managers. Interestingly, many techies who recommend password managers, point out that paper is a safer alternative for our most important passwords. I will join that crowd and say that even if you use a password generating formula, paper still has its place. For what?
If your life savings are in one financial institution, that password clearly deserves special treatment. The password for your main email account is probably more important than your realize. If you do use a password manager, its main password, the one used to access all the other passwords, is special. It is reasonable, if not preferable, to keep your most important passwords away from any type of computing device.
I am not the only techie who thinks there is a place for paper:
"If you use a third party password manager, you might not realize that modern browsers have password management built in with a beautiful UX [User eXperience]. Frankly, it’s harder to not use it. Even if you can’t use a password manager, it is totally acceptable to record your passwords in a paper notebook, spreadsheet, rolodex, or any other method you have available to record data. These are cheap, universally available and accessible."
The lesson from these stories, is that anyone who suggests that one approach is always the best is a fool.
And, if you do use paper, please keep two copies in two different, safe, locations.
In August 2019, the New York Times published an article "Why You Need a Password Manager. Yes, You" which is an example of this tunnel vision. The author, Andrew Cunningham, is a true believer in the only solution. More about this article is below in the Me vs. The New York Times section. Different approaches are a better fit for different people with different needs. And even for a single person, different approaches may make sense for different passwords. The real lesson to be learned is not to get computer advice from the New York Times.
In October 2020, on Episode 1,737 of the Tech Guy podcast, a caller asked show host Leo Laporte, for a good way to remember passwords for a senior citizen. Laporte went through four different approaches for managing passwords, but in the end was forced to admit that none was a great fit for a senior citizen. He never considered a password formula. If you watch the video, the topic comes up 13 minutes 25 seconds into the show.
FYI: Let's debate password managers at the Forums of askwoody.com.
INTRODUCING A FORMULA top
In my opinion, a password formula is a great solution. It solves three problems: it makes retrieving passwords easy and it helps create reasonably long and reasonably unique passwords. A tri-fecta. It is the Rodney Dangerfield of password solutions - it gets no respect.
What everyone has gotten wrong, is thinking of a password as a single thing. My idea/suggestion is to consider a password as a two part thing.
One part never changes, its something meaningful to you that you will never forget (trust me on this). The other part does change but can be very simple and also meaningful to you. That's it. A constant and a variable. This should help you create dozens of unique, yet easily remembered, passwords.
DIP YOUR TOE Section added October 20, 2023 top
For a small scale, simple, example of using a formula, consider the case of having multiple accounts with the same content provider. We all like entertainment, so for the sake of example, consider someone with multiple registered accounts with The Hollywood Reporter. One account is used to track what's going on with movies. Another account is used to track industry-wide happenings. Still another account is used just for news about streaming services.
Using a formula, the three passwords might be
thrmovies thrindustry thrstreaming
Clearly, easy to remember. Every account starts with "thr" for The Hollywood Reporter. On their own, the words "movies", "industry" and "streaming" are miserable passwords, but when paired with "thr" they become much more secure.
OK, an account with The Hollywood Reporter (not sure if they even have accounts, just an example) is not very important. But, if it was important, the
passwords could be made more secure as:
thrMovies thrIndustry thrStreaming
That is, add a capital letter in the middle of the password.
Another step up the security ladder would be
thrMoviesthr thrIndustrythr thrStreamingthr
Here, the constant prefix is also used as a constant suffix.
To use a formula more broadly, we probably should use a prefix (and possibly a suffix) that is not dedicated to The Hollywood Reporter. Unless, your name is Thomas Harvey Randolph, in which case using "thr" as a password prefix/suffix makes a lot of sense :-)
EXAMPLES OF SIMPLE FORMULAS top
Say, for example, that you are a fan of the New York Yankees and your favorite player is Babe Ruth. Fine. Start every password with "BabeRuth". That's your constant. You should write it down in case amnesia sets in, but I doubt you will have any problem remembering that all your passwords start with the name of your favorite baseball player. It should not take too long for this to get burned into your brain.
If you are in the habit of using the name of your pet dog as a password, then instead of it being the entire password, use it as the constant part of every password. Now, all your passwords start with "Fido" or "Rover" or "Daisey". I am using a capital letter in these examples as having at least one makes any password more resistant to brute forcing.
The variable part of your passwords does not need be any more difficult. You can pick what, on its own, is a miserable password. For amazon.com, you could, for example, use "jungle". For Barnes and Noble, you could use "book". For Gmail you could use "geemail".
Putting it all together, our fictional Yankee fan, would have passwords of "BabeRuthjungle", "BabeRuthbook" and "BabeRuthgeemail".
Not the most secure passwords in the world, but probably better than most. And, speaking as computer nerd, I can not stress enough how important it is to not re-use passwords.
Speaking of which ... a formula means never having to re-use a password, even for accounts that you don't care about. Your password for websiteX could be "BabeRuthwebsiteX". This is barely harder than re-using a password, yet its more secure. It's not very secure, just more so.
MORE SECURE EXAMPLES top
These passwords can (and really should) be made much more secure fairly easily.
Just replace the "BabeRuth" constant prefix with "Babe-Ruth" or "BabeRuth--" or "babeRUTH". Many passwords that consist of a single capital letter have it as the first character, so, don't use "Baberuth-".
Likewise, "Fido" and "Rover" can be made more secure by adding a special character or two ("Fido=" or "Rover//"). Heck even just repeating the pet name twice ("RoverRoverjungle"), is a huge improvement.
If you are really ambitious, break up the name into a prefix and a suffix such as "Babe-jungle-Ruth" or "babeBOOKruth". For pet lovers, consider "Fido-geemail-Fido".
And, Joe DiMaggio is better than Babe Ruth - not because he hit more home runs, but because his name is longer (11 letters vs. 8). And Mickey Mantle beats them both; his name is 12 letters long. Lou Gehrig? Barely better than Ruth.
Baseball players come and go, but team loyalties do not. So, Missouri residents can create great Amazon.com/jungle passwords such as "STLcardinalsjungle" or "St.Lcardsjungle" or "StLouisjungleCardinals" or "st.louis.junglecardinals" or "STLjungleCardinals".
Finally, let me note that while you might use an extremely simple word ("book" and "jungle" in our examples) as the variable half for some accounts, your most important accounts deserve something better. If you depend on Gmail, for example, then "geemail" is a bit too simplistic, even as only half the password.
These formula-generated passwords are virtual unicorns: easy to remember, long and, almost definitely, unique.
It's the best password advice in the world.
- - - - - - (Section below added May 26, 2023) - - - - - - -
This article, What's a Double-Blind Password Strategy and When Should It Be Used by Specops Software (published at BleepingComputer.com May 25, 2023) is a sales pitch for Specops password software. Despite that, it discusses using a password formula, with a twist.
First off, terminology. What I refer to as a formula, they refer to as a "double-blind password strategy", "horcruxing", "password splitting" and "partial passwords".
The basic concept they describe is the same as mine, split a password into two parts. However, they suggest storing the varying part in a password manager. They don't consider that the varying part of the password can be remembered. In their world, the varying part of each password is long and complex. Fine. We both suggest keeping a short unique part of each password to yourself.
They note that even if the password manager is hacked, your full passwords are not stored there. This is analogous to my suggestion of writing the variable part of the password on paper. Anyone can see the paper and still not know your passwords.
THREE TYPES OF FORMULAS (Added August 31, 2019) top
To sum up the above, I suggest a formula with a fixed and a variable component. To begin with, the fixed component can be at the beginning followed by the variable part. If you are more ambitious, then create a fixed beginning and a fixed ending, with the variable part in between them. For the lack of a better term, I will refer to this as a soft formula, in that you can always change the variable portion.
Some criticism of formulas assumes another type, which I will call a hard formula. This type, like a mathematical formula, creates one and only one output, for any given input.
For example, assume a hard formula based on a website name. Perhaps the first two letters of the site name and the suffix. So, Amazon.com would generate a password of "am.com" and yale.edu would be "ya.edu". This could be made stronger by appending a fixed constant, yielding something like "BabeRutham.com".
Another simple hard formula might work when you are required to periodically change a password. If you start with, for example, "monkey-1", then, when forced to change it, use "monkey-2" and the next time "monkey-3".
I know of two problems with hard formulas:
I mentioned Gabriel Fair and his five different password solutions for five different classes of password earlier. One solution is a formula, but he uses a hard formula.
Hard formulas are what scares people away from formulas. Specifically, the worry that if a few passwords leak, through the inevitable data breaches, a bad guy might figure out the formula. With soft formulas, even if the formula leaks, you are still safe. So what if the bad guys figure out that my passwords start with "BabeRuth"? That's only half the password.
That said, if you are still concerned about the formula leaking, consider using different formulas for passwords of different importance. That is, use one formula for important websites/systems and a different formula at places that you don't care much about.
For example, a fan of the St. Louise Cardinals baseball team might use a formula with both a prefix and suffix and mixed case letters for important passwords. Something on the order of "StLouis<something variable>Cardinals". For less important passwords, they might only use a common prefix and all the same case. Perhaps "stlouis<variable>" or "STLC<variable>" for their unimportant passwords. (added Feb 21, 2021, punched up Nov. 1, 2023)
A third type of formula is the reverse of the first two. Instead of adding characters to make a password more secure, it subtracts characters.
Suppose, for example, that you have a dog named Fido and none of your passwords include the dog's name. In that case, you could store passwords such as
In a 2020 interview Roger Grimes said "If you don't want to use a password manager you can use a password-protected document. Just don't put your passwords down in plaintext. Use codes like ff32 for frogfrog32. That way if a hacker sees or steals your password document they really don't get your passwords." The concept applies even when using a password manager. (added November 1, 2023)
PASSKEYS (section added Oct 22, 2023) top
In 2023 Passkeys were first introduced to the world. There was a large press campaign in October where every media outlet had an article about how to use passkeys and why they are the greatest thing since sliced bread.
Passkeys will fail. No one will use them. I say this for many reasons, but the reasons are not relevant to passwords.
Still, passkeys do have one advantage over passwords: when a website gets hacked and bad guys get millions of userids and (hopefully encrypted) passwords, they can use the userid/password (aka credential) to not only log in to the hacked system/site but also any other place where a victim has used the same credentials. This is called credential stuffing and there is more about it on my Defensive Computing website.
This danger derives from the fact that a password is a single thing. In contrast a Passkey is two numbers. A website stores one number, your computing device stores the other number. The numbers have a relationship that only a math major can fully understand. Simply put, the relationship is that something encrypted with one number can only be decrypted with the other number. Thus, stealing one number is useless.
Stealing a passkey number from a website is like stealing a lock and not having the key. Or, stealing the key and not having the lock.
A password formula is also two things, two components of the one password, a fixed portion and a variable portion. As noted earlier, this lets you store each half separately and the loss of either half is not a problem, at least not an immediate one.
So, while a password created with a formula is subject to credential stuffing, using a formula makes it very likely that a victim of a data breach will have different passwords everywhere - which means that credential stuffing will fail. The bad guys can use the stolen password to login to the website/system they stole it from, which is not the case with single stolen passkey/number. However, the damage from one stolen password is contained when we have different passwords for each site/system.
However, the idea that passkeys are safer than passwords because bad guys that hack a website only get half of what they need, turns out to be a scam, despite being true.
It can not be a real advantage until systems are developed that only use passkeys. Period. That is, it is not a real advantage until systems/websites do not allow a fallback to a stored password. No such system exists in 2023 and it may never will. Time will tell.
ARGUING AGAINST PASSWORD MANAGER SOFTWARE top
The knee-jerk reaction of techies, is typically to use a password manager. I think a formula is often a better option. Here is why:
"I've spent a lot of time trying to understand the attack surface of popular password managers. I think I’ve spent more time analyzing them than practically anybody else ... Conceptually, what could be simpler than a password manager? It’s just a trivial key-value store. In fact, the simplest implementations are usually great ... Things start to go wrong when you want integration with other applications, or when you want data synchronized by an untrusted intermediary. There are safe ways to achieve this, but the allure of recurring subscription fees has attracted businesses to this space with varying degrees of competence. I’m generally skeptical of these online subscription password managers ... I often say that 'use a password manager' is bad advice. That’s because it’s difficult to tell the difference between a competent implementation and a naive one. The tech press ... can’t realistically evaluate any security claims, so how do you propose users tell the difference? For that reason, I think 'use a password manager' is so vague that it’s dangerous. A good analogy is telling someone with a headache to pop any pills they find in the medicine cabinet ... Advice on this topic needs to be specific. It’s better to recommend implementations that are well designed, rather than general product categories." (added June 10, 2021)
"Despite what your vendor says, if their network is compromised, the attacker can read your passwords. Here are some selected marketing claims from password manager vendors: 'No one apart from you, not even [us], has access to your passwords' ... These claims are all nonsense. An attacker (or malicious insider) in control of the vendor’s network can change the code that is served to your browser, and that code can obviously access your passwords. This isn't far-fetched, altering the content of websites (i.e. defacement) is so common that it’s practically a sport. The reality is that you have to trust your vendor to maintain their infrastructure and keep it safe. The existence of encryption ... does not alter this." (added June 10, 2021)
In response to one of my tweets about this blog, ZDNet reporter Catalin Cimpanu tweeted: "I've always used password formulas. Password managers are on my threat model as a reporter. Can't use them. Unless it's some account on a no-name site that I don't care about, I have a formula-based password for it." Computer security is Companu's beat. He has been covering it for years. He is as well informed on security as anyone.
FYI: How to Switch Password Managers Without Losing Your Data by David Nield for Gizmodo (March 10, 2021). The article explains how to export all your userids/passwords in 10 different password managers. Interestingly, Safari is the worst, it does not let you export everything at once. Instead, you need to copy one userid/password at a time.
In their Creating Strong Passwords article (Oct. 2018), the EFF said "Wondering whether a password manager is the right tool for you? If a powerful adversary like a government is targeting you, it might not be. Remember: Using a password manager creates a single point of failure. Password managers are an obvious target for adversaries. Research suggests that many password managers have vulnerabilities."
SEEING BOTH SIDES OF PASSWORD MANAGER SOFTWARE (section added Nov 17, 2021) top
Even someone who uses and recommends password managers, Daniel Aleksandersen, notes that password managers are a single point of failure and are difficult to back up. See How to back up your password manager. (Feb 17, 2020)
On April 2, 2020, computer expert Robert Graham blogged about an issue with Zoom possibly stealing passwords. This led him to discuss good password practices, in general. He said: "By far the most important thing you should do to protect yourself from Internet threats is to use a different password for all your important accounts, like your home computer, your email, Amazon.com, and your bank. Write these down on paper ... Don't print them, don't store them in a file on your computer ... Store copies of that paper in a safe place. I put them in a copy of the book Catcher in the Rye on my bookshelf ... Writing it on a Post-It note taped under your keyboard is adequate security if you trust everyone in your household." In the article he does recommend Password Managers but, he knows all too well the things that go wrong with software and that some things are too important to trust to a computer.
Bruce Schneier, who wrote his own password manager program, realizes the inherent risks to such software. In June 2019 he described how he deals with this risk: "My particular choices about security and risk is to only store passwords on my computer - not on my phone - and not to put anything in the cloud. In my way of thinking, that reduces the risks of a password manager considerably. Yes, there are losses in convenience." As I noted here elsewhere, you can not have both security and convenience. (added paragraph Nov 17, 2021)
- - - - - - - - - - - - (added the Schechter article Nov 17, 2021) - - - - - - - - -
In June 2019, Stuart Schechter wrote a great article on the pros/cons of password managers: Before You Use a Password Manager. It begins with:
"I cringe when I hear self-proclaimed experts implore everyone to 'use a password manager for all your passwords' ... As most of us who perform user research in security quickly learn, advice that may protect one individual may harm another. Each person uses technology differently, has a unique set of skills, and faces different risks."
I agree completely.
It is a long article that begins with the benefits and risks of using a password manager. Then it covers protecting the data in a password manager, and having a recovery strategy for that data. He then suggests starting off with a password manager for a few un-important passwords, to get the lay of the land, so to speak. He ends with the list of decisions that need to be made when using a password manager. The list is below and clearly shows that the software is not for everyone.
- - - - - - - - - - - (added this January 8, 2023) - - - - - - - - -
In January 2023 there was a discussion on the Ask Woody Forums about disengaging from Last-Pass. Forum user Paul T, suggested this list of questions to ask yourself before deciding on a particular password manager. Not an easy decision and, no doubt, some people will pick a Password Manager that is not right for them.
DO NOT USE LASTPASS (section added Jan 2, 2023) top
If you want to use Password manager software, do not use LastPass.
While most of this write-up involves making logical arguments, this section is just a short heads up. The final straw for many was the breach they announced just before Christmas 2022. Some think the timing of their announcement was to minimize press coverage. But, that breach is only the tip of the iceberg, I would have recommended avoiding the software and the company long before the end of 2022. There is much that could be added here, but again, this is just a heads up.
This paragraph was added here August 25, 2022
Here are some articles about the Christmas 2022 data breach.
In February 2022, we learned more about the Christmas breach. From Dan Goodin for Ars Technica: LastPass says employee’s home computer was hacked and corporate vault taken. The company violated a cardinal rule: work belongs on one computer and personal stuff on another computer. An employee, one of only four in the company with top level clearance, did corporate work on his personal computer. The PC got hacked and then the company got hacked. There is no excuse for this.
ARGUING FOR PASSWORD MANAGER SOFTWARE (section added Oct 10, 2019, last updated Oct 12, 2023) top
A password manager that automatically enters passwords for websites, can protect against scam websites. Many people do not know the rules for domain names and thus can be tricked into thinking a scam website is legitimate. I explain the rules for domain names on my Defensive Computing Checklist web site.
For example, a saved password for citibank.com will not be automatically entered at citibank.badguy.com or secure-citibank.io. The protection is not foolproof however, a victim may think there is a problem with the password manager and manually enter their password.
A great use of a password manager is to pass on your passwords after your death. Simply give your trusted person the master password and tell them how to access the software. As new accounts are created and passwords are changed on old accounts, the trusted person does not have to be given any updates. This scheme also works if, over time, you stop trusting someone to handle your affairs after your death. Should this happen, just change the master password and give the new one to your newly trusted person. (para added Oct 12, 2023).
- - - - - -
A undated (probably from 2019) white paper Modern password security for users by two Google employees (Ian Maddox and Kyle Moschetto) argues in favor of password manager software. This is a classic example of advice from techies for techies that is not appropriate for many people. Their advice on evaluating the software and how to use it, is making my case for me.
For example, they say: "A common criticism of password managers is that all of your secrets are in one high-value target. Losing control of that vault means losing control of all the accounts that it contains. This is why it is important to choose a password manager that has a high level of trustworthiness, transparency, and multiple layers of security controls." If you can evaluate software by these criteria, fine. If not, then password management software is not for you.
In addition, they advise keeping an offline copy of the recovery codes that you can use if the master password for the password manager is lost. And, to make sure the devices that have access to your password manager are secure and kept up to date with the latest patches. After all, they say, your overall security is only as strong as the weakest link. Agreed. Consider this advice table stakes for playing in the password manager game.
They suggest that the features below are the minimum requirements for a good password manager:
Going beyond the bare minimum, they suggest looking for a password manager with these extra features:
Not sure what self-hosting refers to. Ditto for behavior-based security.
I do not disagree with the advice from Maddox and Moschetto. If you want to manage your own encryption keys, fine. My point, again, is that there are very few people able to understand and implement these suggestions. And, anyone not able to grasp or carry out their advice is asking for trouble by using password management software.
They did give some examples of formulas. Starting with the simple password "mango2", they suggest:
Being techies, they say nothing about using a paper and pencil for saving passwords. And, being Google employees, they fail to point out the danger in web browser extensions, the next topic. Could it be because Google is so heavily invested in the Chrome browser?
- - - - - -
This article, Can Your Password Manager Be Hacked? (by Roger Grimes Jan 18, 2021) is yet another example of someone who has drunk the Kool-Aid. While Grimes admits to some danger with password management software, it is the only password solution on his radar screen. This is the very definition of thinking inside the box. He admits that a password manager is a single point of failure, but he blows it off rather than suggesting ways to protect yourself. And, like other people that argue in favor of password managers, he ignores the dangers of a browser plug-in. Back in 2018 Grimes, offered yet another poor argument (Using a password manager: 7 pros and cons). On the pro side, he cited both better security and ease of use. This is never possible, whenever you increase one, the other decreases. He is selling snake oil. Finally, his worst case scenario is forgetting the master password. Apparently he has never experienced a software bug or a memory error or a broken keyboard. And here too, nothing about planning for the worst. All told, two lame articles that boil down to: it's better than re-using passwords. For some people, yes. But not for all and certainly not for many.
LIE TO YOUR PASSWORD MANAGER (section added Feb 13, 2022 | Updated Feb 11 and Nov 2, 2023) top
LIE ABOUT PASSWORDS
Security questions, things like the name of your best friend as a child, have mostly disappeared. But dealing with them offered a good lesson: lie. The best way to deal with security questions was to treat them like a second password. When asked the name of a person, give the name of a place. When asked the name of a place, use the name of a person instead. Truthful answers opened you up to hacking from people who could research a truthful answer.
Greed may have been good in the movie Wall Street, but lying is good Defensive Computing.
With that in mind, I recently ran across this article: Peppering Your Passwords In Your Password Manager: How-To Guide. It was written in April 2021, by someone who prefers to be anonymous. Simply put, it suggests lying to your password manager and I think that is a great idea.
Terminology: what the article calls a "pepper" is nothing but a common suffix/ending for the passwords stored by the password manager software. An ending, that the software does not know about. To me, its a useless term that makes the simple complicated.
This concept is also discussed in the section on three types of formulas. The third type is a formula for lying about your passwords when you save them.
Like a formula for creating passwords, this idea treats the saved password as two things rather than as a single thing. When you do this, the password manager software does not know the real password, but you can derive the real password from the saved one, with a formula.
Perhaps you omit part of the password, such as a fixed prefix or fixed suffix, when saving it. Perhaps you do the reverse, add a fixed string of characters to the saved password, that you know does not belong in the actual password. There are examples of this in the Three Types of Formulas topic.
If you like the idea, the next issue is whether to do it all the time or only sometimes. Adding extraneous characters seems like the best solution if you only want to lie about some saved passwords. When doing this, it is obvious which saved passwords have the extra characters and which do not. This not at all obvious when the saved password has fewer characters than the real one.
If you prefer a common prefix or common suffix, do you use the same one all the time or two different ones? Maybe a short fixed component for un-important passwords and a longer one for the important ones? No one right answer.
The concept of storing the wrong password applies to whatever technique you use for storing passwords. Despite the title of this section, it is not at all limited to password manager software. Heck, it is probably best used when storing passwords on paper, especially since the extra characters can be in the beginning, middle or end of the stored password.
The worst suggestion made in the article cited above is to let the password manager software auto-fill your passwords. On websites, this a huge security risk as it gives the browser extension far too much access to every web page in your browser. More on this in the Browser Extension section below. This is yet another example of ease-of-use being in conflict with security.
LIE ABOUT USERIDS
Password managers store both a password and a matching userid. For years, I have been lying about the userid to the password manager that I use. You should too.
For example, there are many websites/systems where the userid is an email address. Rather than store my email address in the password manager, I might just store "me". I also have multiple email addresses. So, at times, I will store something like "me at yahoo" or "me at aol" in the userid field.
When the userid is not an email address, I sometimes pad it. Suppose, for example, my userid for a site/system was "mikey9". If I can remember the userid, I will store it in the password manager as "mikey9x" or "mikey9123" I can't remember every userid of mine, but I use this padding for the ones I can remember. For ones that I can not remember, I make the padding more obvious, something along the lines of "mikey9------xyz".
PASSWORDS CAN BE TOO SECURE (section added February 17, 2022) top
Hopefully, by now, you have reviewed a number of approaches for dealing with passwords, all with the goal of using the most secure system possible.
But is that the only goal? After I wrote the section above (lying to your password manager), Royce Williams, playing devils advocate, wondered if that creates a system that is too secure. Too secure?
It has happened, and surely will again. A person with a super secure password scheme becomes incapacitated or passes away and their spouse/family is locked out of all sorts of important files and records. For more on this, see a talk given by Andrew Kalat back in 2016 called Online, No One Knows You're Dead.
BEWARE OF BROWSER EXTENSIONS top
Many password managers install a browser extension to handle passwords in web pages. These extensions have carte blanche. They see everything on every web page. And, they can change it. They are the Queens of the chessboard. This, to me, is an accident waiting to happen.
The permissions of browser extensions are usually hidden. Normally, you see them only when the extension is first installed. With the Chrome browser, the Queen-level permission is "Read and change all your data on the websites you visit". Let that sink in. I checked four Chrome password manager extensions (Avira, Lastpass, Bitwarden and Dashlane) and each required this permission. What if the vendor of the password manager gets hacked? Or, their supply chain gets hacked? Or, they make an honest mistake? With such a powerful extension installed, you are living on the edge of a cliff.
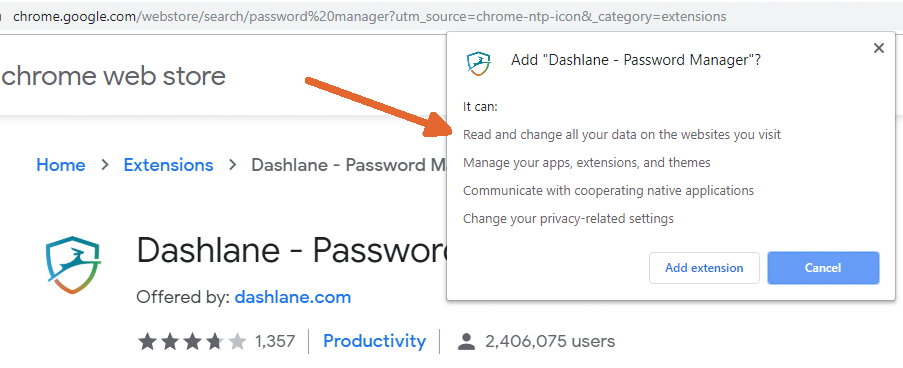
Plus, there are some Chrome browser permissions whose meaning is not at all obvious. Dashlane, for example, not only wants to read and change everything on every page, it also wants to:
Unless you fully understand what these permissions mean (I do not) you can not make an informed decision as to whether this lowering of normal browser security is worth the convenience offered by the Dashlane password manager. You will never see anyone make this argument. I very much doubt that anyone who recommends password manager software has thought things through to this level.
FYI. Mozilla explains the assorted permissions for extensions in Firefox here Permission request messages for Firefox extensions.
Update September 16, 2019: LastPass bug leaks credentials from previous site by Catalin Cimpanu. A bug in their browser extension exposed credentials entered on a previously visited site.
Update January 20, 2020: Avast Online Security and Avast Secure Browser are spying on you by Wladimir Palant (October 2019).
Update January 23, 2020: From Ars Technica More than 200 browser extensions ejected from Firefox and Chrome stores. Firefox ousts almost 200 add-ons while Google detects a significant increase in abuse.
Update March 3, 2020: From Brian krebs The Case for Limiting Your Browser Extensions.
Update October 25, 2020: Adblockers installed 300,000 times are malicious and should be removed now from Ars Technica. A popular browser extension was sold and the new owner made it malicious. There is no way for people using any given browser extension to know if this happens. Quoting the article: "It’s hard to provide actionable advice for preventing this kind of abuse." Me: avoid browser extensions that have full access to every web page. Many/most do. But not all.
Update May 25, 2021: Daniel Aleksandersen is a techie's techie. On May 24, 2021 he warned about passwords in browsers: "I've recently had a change of heart regarding having my password manager available for auto-fill in my web browser. Password manager extensions and password managers built into web browsers are very convenient. Web browser-integrated password managers - both the built-in ones and extensions - have suffered from many auto-fill leaks and vulnerabilities over the years. It’s an attack surface I can do without."
Update June 10, 2021. As noted elsewhere on this page, Tavis Ormandy, who works for Google, is a techies techie. The excerpt below is from an article he wrote about Password Manager software in June 2021. Specifically, he describes the integration of a Password Manager with a web browser.
"There are two primary components that make up your browser interface, the chrome (confusingly, the term has nothing to do with Google Chrome) and the content area. The chrome contains things like the address bar, tabs and back button. These components can be trusted, and websites can't interfere with them. Conversely, anything inside the content area can be controlled by the website and therefore it can't be trusted. Most password managers blur this distinction by drawing their UI in the content area. There is just no way to do this safely ...
We've already established that one component of online password managers must be injected into potentially hostile environments. How can those components communicate with other components? One naive solution would be to just use XHR or WebSockets to a local HTTP endpoint. This sounds appealing to developers, they’re the native way to communicate on the web. The problem with this solution is it's very difficult to differentiate between your content script, and a hostile script running on the same page but a different world. Essentially every implementation I’ve looked at has got this wrong, resulting in critical game-over vulnerabilities.
Another gripe I have with online password managers is that they render browser sandboxes less effective. Modern browsers use a sandbox architecture to isolate components that can go wrong. The problem is that online password managers effectively inject privileged components into these sandboxed processes with extensions. The purpose of sandboxing is to isolate potentially compromised components from each other, but if you stuff all your most valuable secrets inside the sandbox - then what’s the point? I worry that people don’t understand the tradeoff they’re making here."
Update September 3, 2021. This article Is LastPass Password Manager worth using? (Ghacks.net Aug. 2021) points out that the LastPass browser extension wants to spy on you. There are two deeply buried options that can turn this off (see Step 9: Disable telemetry in the article).
Update March 16, 2023: This article in PC World points out a technical complication with browser extensions that fill in your password.
Don’t use autofill on your password manager - especially if it’s Bitwarden by Alaina Yee (March 15, 2023)
A web page is not a single thing, it consists of many parts, sometimes dozens, drawn from many different sources. Some web pages contain min-web pages in an HTML entity called an IFRAME. What if the box where the password is entered, is not from the same domain as the web page itself? Your browser could show you are at abc.com but the form where the password is entered could have been loaded from def.com. What to do? Should you trust def.com?.
Security firm Flashpoint blogged that Bitwarden did trust def.com and did not even display a warning. This is a classic case of ease of use vs. security. Bitwarden made this decision for ease of use. It is, after all, a commercial product (with a free component).
Why do browser extensions exist for password managers? Convenience. I have been a computer nerd for more years than you would believe, and trust me, that convenience is the enemy of security. Nothing is both secure and convenient.
No Crappy Passwords - Software for Windows and Linux (section created October 17, 2022) top
Software called No Crappy Passwords is somewhat like using a formula.
You start by creating a nickname for every system/website that needs a password. Something like: SusanChecking, MyMastercard, HusbandsAppleid, Yahoo. To this you add a fixed constant that the software refers to as an "offset". Unlike a soft formula, where the fixed portion can be anything, here the fixed constant can only be a number. You enter these two things into the software and it spits out a random-enough password.
So, it starts with the same two halves of a password as a soft formula. What the software adds, is that it takes these two simple short things and creates a long ugly password from it. You then copy/paste the generated password from the software into wherever it goes.
Sounds good, at first. I especially like that there is no browser extension and no cloud component. You can also tell the software how long the generated password should be.
Like hard formulas, it might seem that generating a new password for the same account would be a problem. While the software can not handle that, there is a work-around - create a new nickname for the existing account. So a MasterCard account that was known as HarveyMastercard will now have to be called HarveyMastercard2 (or something to that affect) to enable the software to create a new password.
With this software, you would probably need to write down the nickname for every account. While we can recall a few nicknames, we all need 300 passwords and there is no way to remember 300 nicknames. If you forget the nickname, you have, in effect, forgotten the password. As with a soft formula, writing down the nicknames is safe, because it does not include the fixed "offset".
But . . .
The software only runs on Windows and Linux, which is pretty restrictive. And, it generates passwords with special characters which can be a problem. There are many places where assorted special characters are not allowed and there is no way to limit the special characters that the software creates. The use of the term "offset" is not particularly friendly for non techies. The software is fine when you get to pick your own password, but if you use a website/system that provides the password to you, this software is useless. A soft formula allows for both a fixed prefix and a fixed suffix, this software has only one fixed component. And, there is no way to export the passwords, which is a very big deal.
One of my big gripes with Password Management software is simply trusting software. This program offers a great example of why we should not trust software. At some point in its life, the software was updated. The new version (10.0) will generate a different password with the same inputs. Ugh.
WHAT I DO (section drastically updated Oct 24, 2023) top
Needless to say, all my passwords are different. I have not re-used a password in roughly 30 years.
As I noted in the introduction, the right password solution is likely to include more than one approach. My passwords fall into these different categories with each treated differently.
On my phone, I fell victim to one of the dangers of password manager software - the software vendor walked away from the app. It was free, they were not making money from it after all. I was orphaned. I did not test whether the app would still function, instead I switched. Lots of typing on a glass keyboard :-(
In the dip your toe topic I discuss a very simple formula for multiple accounts with The Hollywood Reporter. I use this sort of formula.
I have more than my fair share of Windows computers and each has a unique logon password (but not a unique Windows userid). My formula uses a fixed prefix (easily remembered) and I use the laptop model number as the password suffix. So, an HP x360 laptop has a login password of "fixedthingx360". A ThinkPad T480 has a login password of "fixedthingt480". Not the strongest formula, but the computers rarely leave my home. Whenever possible, I travel with a Chromebook.
Taking a step back, dealing with hundreds of passwords is not the only issue we all face. To avoid putting all my eggs in one basket, I also use multiple email addresses. I own a domain, one without my name in it, and I typically create new email addresses at that domain for new accounts. (Added March 11,2021)
Again, I am not you. What is right for me is unlikely to be right for you. Hopefully, this topic gets you thinking.
FORMULA vs. SQRL (section added September 27, 2019) top
As I write this in September 2019, Steve Gibson has just started promoting a new identity system called SQRL (pronounced Squirrel). Basically, it competes with passwords. Maybe it will take over the world, maybe it will be ignored. No one knows at this stage. It requires software to be installed both on a web server and the end user computing device, which certainly will be a hurdle to its adoption. Time will tell.
Frankly, I don't fully understand SQRL. It uses the now classic concept of a public key and a private key, two numbers with a relationship between them that seems magical to non-math people. SQRL creates a public and private key pair for each website where the SQRL user has an account. The website only knows the SQRL public key. Thus, if a website using SQRL gets hacked and leaks your public key, no big deal. The public key is not the whole SQRL proof of identity, its only half of it. This is analogous to writing down your password when using a formula. You only need to write down the variable component which is half the actual password. If someone sees the variable half of the password, they can't use it without the fixed component.
Also, in the SQRL system, each person gets a single userid that is used for every website where they have a SQRL based account. In Gibson's lingo, the SQRL userid is a 256-bit master key. Sounds a lot like the fixed component of a password formula which is also used at every website.
Formulas have two advantages over SQRL: they are not limited to websites and they do not require software to be installed.
- - - - - - - - - - - - - - - - -
ME vs. THE NEW YORK TIMES (section added August 29, 2019. Updated Aug 30, 2019)
Now I know how Al Pacino felt in the last Godfather movie. Just when I thought I was done, they drag me back in.
They, in this case, is the New York Times. On August 27, 2019 they published: Why You Need a Password Manager. Yes, You by Andrew Cunningham. The story was originally published three weeks earlier at the Wirecutter which the Times owns.The article in the Times does not allow comments. The Wirecutter does allow comments, and I made one pointing to this very blog. It was quickly removed, which, in a nutshell, tells you everything you need to know about the Wirecutter.
A tweet of mine about this, generated a response from Andrew Cunningham the author of the article: "I’m not going to go point-by-point here but I don’t think this is workable advice for the vast majority of computer users". By not debating, he helps makes my point for me. I don't pretend to know what is best for the vast majority of computer users. Fortunately for them, Cunningham does know.
Perhaps the most offensive thing about this article is the total belief in the one true solution. It does not consider, or even mention, using a formula to generate passwords. I have listed 14 problems above with password management software, yet the article mentions none of them.
STILL MORE PROBLEMS WITH PASSWORD MANAGERS top
Three arguments against password manager software, that I had not considered, were raised by people commenting on the Wirecutter article.
Someone calling themselves Joe said: "So what happens if I set up a password manager and then find myself needing to log into a site/account from a machine that is not mine? Perhaps a family member's whom I'm visiting? Since the password manager has created all the passwords for me, how can I hope to know what the password is when I'm not using the manager?" Good point.
Someone calling themselves Rick said: "What happens when you decide you no longer wish to use 1Password, Lastpass, Dashlane etc. as your password manager? Can you transfer your password vault to another provider? Can you transfer them back to the sticky note filing system you used to have?" This generated a link to a possibly helpful article, but still, it would be a hassle that does not exist when using a formula.
Someone calling themselves Michael Rooney cited a glaring exception to the article: " ... who owns the various password managers and how is the user protected from them being purchased by someone else?" The only way to insulate yourself from a change in ownership is with software that only runs locally, has no on-line component and never gets updated. If, if, if. This is not a theoretical issue.
LastPass was purchased by LogMeIn Inc. in 2015. What was a small start-up is now part of a large conglomerate. This is a cause for concern. Being part of a large company there is no way to judge the quality of the software. When a product is developed by a small group, or a single person, you can form an opinion of how good and trustworthy they are. This is not possible when the software is in the hands of faceless programmers who, likely, rotate into and out of it. Current Lastpass users are trusting both LogMeIn and, perhaps, their corporate partners too. As a company, LogMeIn has been moving away from consumer oriented products towards Enterprise markets. For example, they purchased GoToMyPC.
Update Dec 19, 2019: Yet again, LastPass was sold. By mid 2020 the software will be owned by "... affiliates of Francisco Partners, a leading technology-focused global private equity firm, and including Evergreen Coast Capital Corporation, the private equity affiliate of Elliott Management Corporation...". Do you trust these nameless faceless owners with ALL of your passwords?
Update: January 20, 2020. It seems that LastPass is not trustworthy. They suffered an outage and did not come clean about the problem.
Reader Richard Belew was hesitant to use password manager software and wrote: "... please create a list of other plausible mechanisms, and publish again".
And these are the comments the Wirecutter let stand. Since they deleted my comment, chances are they deleted others too.
Another article arguing for password managers, generated another reader comment against them. Quoting: "I'm a huge believer in using a Password Manager. I've been a LastPass user for many years. I'm now searching for a different one due to the fact that their 'new interface' is abominable compared to the old one. Where it took one click before, it now takes three. Does that sound petty? Maybe. But hubs is technologically challenged and no longer wants anything to do with LastPass. I have to admit, I can't stand the new interface and don't really want anything to do with it anymore either ... I'm all for change when it's for the better but in this case, LastPass is a major fail...and I'm searching for a suitable replacement."
- - - - - - -
For more Defensive Computing advice, see my DefensiveComputingChecklist.com website.
| | ||
| @defensivecomput | TOP | Home => The BEST password advice |
| michael--at--michaelhorowitz.com | Last Updated: June 3, 2024 10PM UTC | ||

Copyright 2001-2024 |
Copyright 2001-2024 |